
The least we can say is that it was a hot summer for crypto crime! Nearly one billion dollars was swept away between July and September.
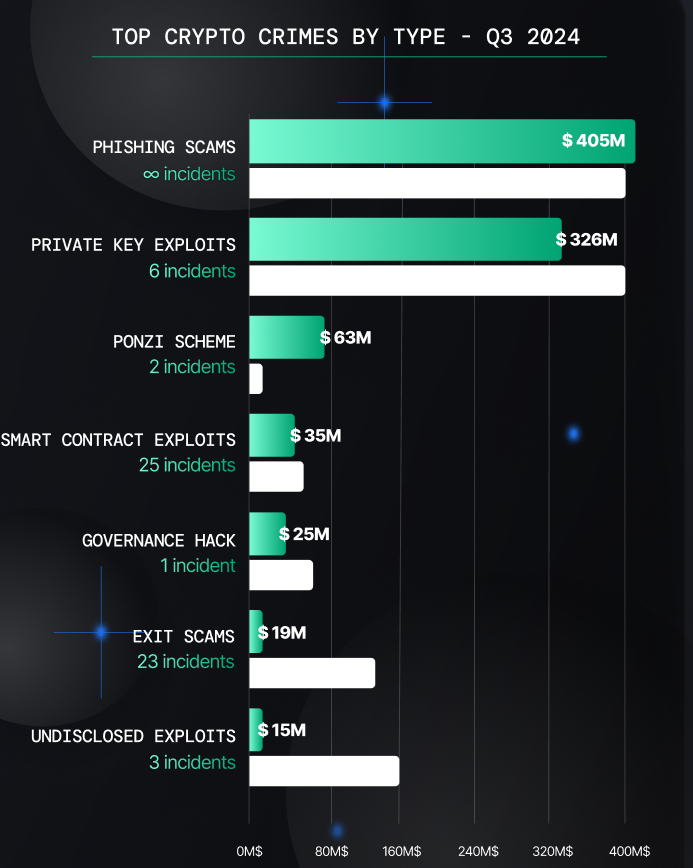
Almost as much was lost in phishing scams ($405 million) as in hacks ($441 million), accounting for the bulk of Q3 2024’s successful criminal activity.

These staggering figures are perfectly in line with what the crypto ecosystem has experienced so far in 2024. We are just one hack away from surpassing the $3 billion threshold in losses for 2024, which could make this one of the most damaging years in crypto crime history after the criminal feist that was the year 2022.
The majority of the criminal bounty in Q3 2024 came from private key exploits, once again proving these to be the most lucrative hacks in the crypto underworld. With just six incidents, these exploits netted over $326 million, accounting for more than three-quarters of the total losses from crypto hacks in Q3 2024.
The main culprit, unsurprisingly, is North Korea’s state-sponsored hacking group, Lazarus. Blockchain security researchers have linked the Lazarus Group to 3 of the top 4 hacks of Q3 2024, with the top two being private key exploits, both targeting centralized exchanges, which have newly become their target of choice.
Unfortunately for the crypto space, another type of threat — and new threat actors — from North Korea has also been emerging. This new DPRK malicious project was relatively dormant at the beginning of the year but came into full effect this summer with multiple high-profile attacks being carried out.
While crypto actors faced a double threat from North Korea, retail investors were actively siphoned off, primarily through phishing, unstoppable wallet drainers, and social engineering attacks. This culminated in the largest phishing incident in crypto history, with more than $240 million lost in a single attack targeting an individual.
The only good news this month is that the $30 million reentrancy attack on Penpie could have been much worse — experts estimate they could have lost close to $100 million in this exploit.
In today’s report, we will aim to provide an accurate overview of what transpired in the realm of crypto crime during the summer of 2024 and recount its most significant stories.
Q3 2024 Crypto Hacks Landscape: The Reign of Private Key Exploits, New Money Laundering Players, and Escapable Hacks
In line with what we have seen since the beginning of 2024, private key exploits have been dominating the crypto criminal landscape, already surpassing their previous damage records.
In 2023, although private key exploits were already the most damaging hacks in the crypto space, they ‘only’ resulted in $555 million lost across 24 hacks. As of Q3 2024 — with $326 million siphoned through 6 exploits this summer alone — private key exploits have already accounted for more than $956 million across 31 incidents.
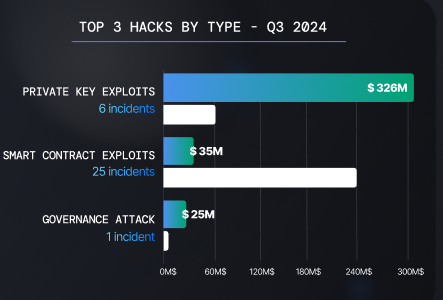
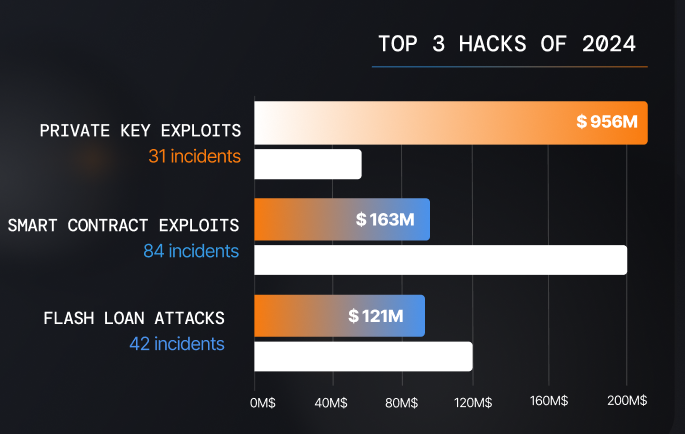 Top Hacks 2024 — Source: Nefture
Top Hacks 2024 — Source: NeftureAgain, unsurprisingly, the North Korean state-sponsored hacking group Lazarus is rumored to be behind 5 of the 6 private key exploits witnessed in Q3.
Although their exploit techniques seem familiar, North Korea’s threat to the crypto space extends beyond the Lazarus Group. They are now equipped with even more sophisticated tools, allowing them to target a broader range of victim types and sizes, making their activities more widespread and threatening than ever.
That’s what we will discuss in detail in the first part of our three-part series dedicated to the crypto hacks landscape in Q3 2024. We will also address new developments on the front of money laundering, as well as two double hack cases witnessed during this past summer.
Q3 2024 Private Key Exploits: The Summer of CEXecutions
In 2024, the biggest change the Lazarus Group brought to the crypto crime scene was its shift in target. In the early days of the crypto era, centralized exchanges were a security nightmare, making them the perfect target for criminals, as we recount extensively in our report ‘Mt. Gox Unveiled: The Real Story a Decade After the Collapse.’
Since then, much has changed, and CEXes have now taken on the allure of impregnable fortresses.
Naturally, DeFi protocols — with too often minimal security processes — become then the target of choices. Lazarus Group made its biggest coup and, conversely, operated the biggest crypto crime ever committed by exploiting the Ronin network for $624 million.
But it appears the Lazarus Group has found the holes in those impregnable fortresses and is actively breaking in.
The Two Biggest CEX Private Key Cases of Q3 2024, Courtesy of the Lazarus Group (Allegedly)1 — WazirX Private Key Exploit: A $235 Million Heist
On July 18th, 2024, Indian centralized exchange WazirX lost $235 million from a multisig wallet. The biggest hack the summer of 2024 saw.
In the early hours of that day, Wazir saw a total of $234.9 million siphoned from its Safe multisig wallet to a new address, with each transaction’s caller being funded by the mixer Tornado Cash.
All the stolen cryptocurrencies were immediately swapped for Ethereum, a signature move of the Lazarus Group.
According to WazirX’s claims, the wallet breach happened because of discrepancies between Liminal’s interface data and actual transaction contents, allowing a hacker to gain control of the multisig wallet and steal funds despite using the Gnosis Safe multisig and a whitelisting policy.
Liminal pushed back against WazirX’s accusation, stating that the “incident originated from an external source” and that the compromised multi-signature smart contract wallet used in the attack was “created independently and later imported onto the Liminal platform.”
While the details of what really happened are still murky, cybersecurity company CYFIRMA identified the North Korean Lazarus Group as the culprit behind this exploit.
As of October 3rd, 2024, the WazirX hacker has laundered almost $230 million through Tornado Cash, most of it during the month of September, leaving barely over $5 million remaining in their main wallet.
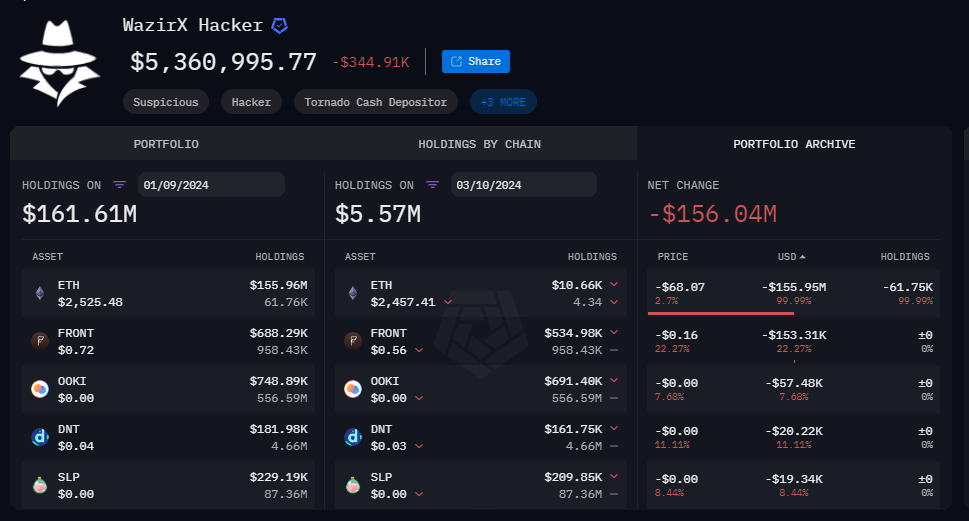 Wazirx Hacker Main Wallet Holdings — Source: Arkham
Wazirx Hacker Main Wallet Holdings — Source: Arkham2 — The BingX Private Key Exploit: A $52 Million Heist
On September 20th, 2024, Singapore-based CEX BingX suffered a private key exploit amounting to $52 million.
It was a two-fold attack that took place hours apart and targeted one of the exchange’s hot wallets. Cyvers suggested that the post-heist obfuscation technique closely resembled a Lazarus Group pattern.
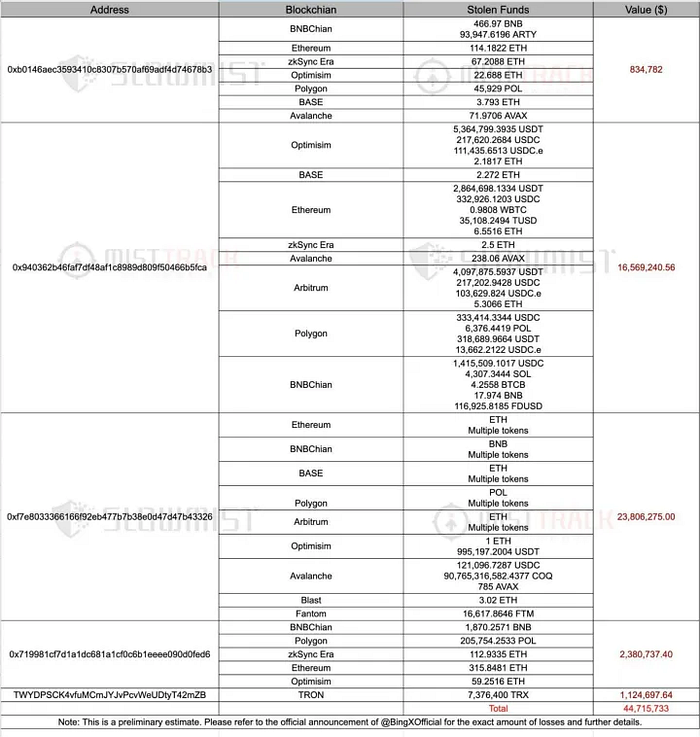 Part of Funds Stolen During The BingX Heist — Source: SlowMist
Part of Funds Stolen During The BingX Heist — Source: SlowMistLazarus heist aside, the BingX team received heavy criticism for its management of the crisis — from initially hiding the heist behind a ‘temporary wallet maintenance’ notice to downplaying the loss as a ‘minor asset loss’ when it had already been revealed that more than $50 million had been siphoned. In reality, the ‘minor loss’ amounted to more than 1/8 of their funds, if Arkham’s figures are correct!
The post-heist efforts, mounted with blockchain security firms and similar partners, nevertheless succeeded in freezing around $10 million.
As for how both these private key exploits and other attacks occurred, the Lazarus Group has developed a well-oiled social engineering machine over the past few years.
North Korea, Social Engineering and Organized Targeted OperationsWith their 2024 crypto heist, the Lazarus Groups has reached a mind-blowing record: they successfully thieved more than $3,7 billion over the past 3 years, essentially through social engineering techniques.
It was through a simple PDF and a fake job offer that the biggest heist in crypto history took place in 2022 when Ronin Bridge lost an astounding $624 million.
Web3 companies are particularly vulnerable to devastating private key exploits, as a recent report from Web3 firm De.Fi reveals. According to the report, governance framework mispractice poses a threat to 75% of top tokens.
Only 16.6% of the contracts analyzed were managed by multisig wallets, which require up to five different private keys to approve any transaction. Multisig is not even a sophisticated security tool; using it is the most basic security step of any protocol to safeguard against inside jobs, social-engineered or not, scams, and hacks.
Although this report primarily concerns tokens, it accurately represents the lax approach to security practice in the entire Web3 landscape. A lack of security measures proves to be a key factor in most private key exploits through social engineering or otherwise, as only one compromised wallet is needed to compromise a whole protocol or CEX.
A private key — governance security so lax, that, for instance, FTX faced a $447 million hack in November 2022, where the attackers reportedly simply sim-swapped one individual to gain access to the private keys and wallet from which they would withdraw the funds from FTX’s coffer. Later, it would be revealed that FTX stored private keys without encryption.
The lax security practices have become the Achilles’ heel of the crypto space, and North Korea’s state-sponsored crypto hacking group, Lazarus, quickly caught on to this.
Private key exploits through social engineering have become their crypto villain signature.
1.Contagious Interview — The first social engineering technique they developed is targeting job seekers.
Dubbed “Contagious Interview” by Unit 42 researchers, the first campaign involves attackers posing as employers to trick software developers into installing malware during the interview process, potentially leading to various types of theft. This strategy has been a key element in some of the most significant heists orchestrated by the Lazarus Group, netting them billions.

The compromise of private keys by the Lazarus Group is most of the time not recognized by the victim parties, especially centralized entities, until the FBI, a security researcher, or a security company comes forward to unveil it. The specific details of how it occurred were never fully disclosed, except for one case: the CoinsPaid hack.
Similar to the Ronin case, the private key exploit was made possible through malware implemented via ingenious social engineering tactics.
On July 22nd, 2023, the Lazarus Group stole $37 million from the Estonia-based cryptocurrency payments firm CoinsPaid via LinkedIn.
According to CoinsPaid’s post-mortem report, the Lazarus Group initially attempted to breach their systems through conventional hacking methods starting in March 2023.
After months without success, they reverted to their successful tactic: the fake job offer route.
 CoinsPaid Hack Timeline — Source: CoinsPaid
CoinsPaid Hack Timeline — Source: CoinsPaidThey dangled extremely appealing high-salary job offers in front of CoinsPaid’s employees, with compensation ranging from 16,000–24,000 USD a month, and waited for an employee to fall into their trap.
An inattentive? Unaware of the risk? Employee took the bait and had a fake job interview with them, during which he was asked to download software to complete a technical task.
Unfortunately, he did not conduct his job interview using his own personal computer but instead used one that provided access to CoinsPaid’s infrastructure.
The “software” was a malicious code that allowed the Lazarus Group “to gain remote control of a computer for the purpose of infiltrating and accessing CoinsPaid’s internal systems,” per CoinPaid.
After gaining access to CoinsPaid’s infrastructure, they were able to successfully open a backdoor that “allowed them to create authorised requests to withdraw funds from CoinsPaid hot wallets.”
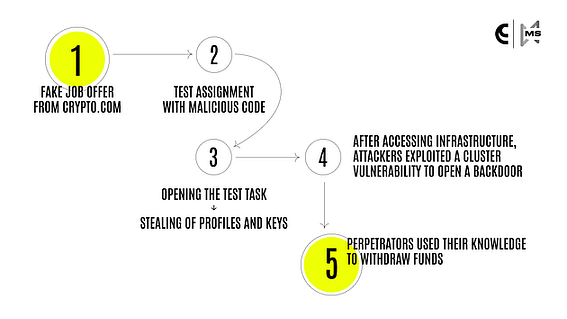 Source: CoinsPaid
Source: CoinsPaidThat’s how $37 million was lost to the Lazarus Group.
This technique of finding weaknesses in people rather than code has proven to be fruitful.
So much so that concomitantly to their contagious interview approach, they launched a new kind of social engineering campaign, this time around, targeting recruiters.
2. Wagemole — The second social engineering campaign, dubbed “Wagemole,” by Unit 42, involves threat actors infiltrating organizations through unauthorized employment, with the dual aims of financial gain and espionage.
Unit 42 has discovered that North Korean moles are using fake resumes to target a wide range of U.S. companies and freelance job marketplaces, utilizing different U.S. VoIP numbers for contact.
Their resumes link to well-maintained GitHub and LinkedIn profiles, making the accounts appear legitimate through frequent updates and interactions. These fraudulent job seekers target on-site jobs but claim to be U.S.-based while temporarily abroad due to COVID, allowing them to ‘work remotely’ for many months — long enough to siphon intelligence and funds.
Their activities extend beyond the U.S., targeting global freelance markets, including Africa. Unit 42 has also identified that they use multiple accounts on various platforms and attempt to buy or borrow high-reputation accounts to conceal their true identities and win job bids.
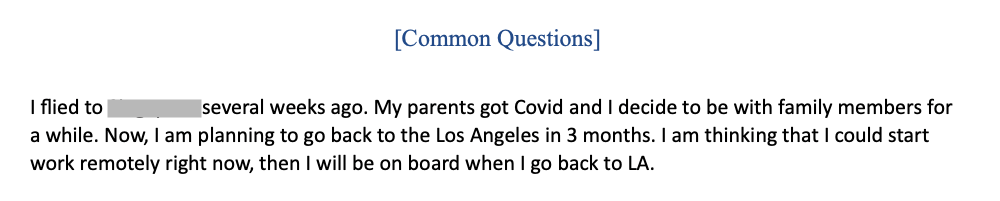
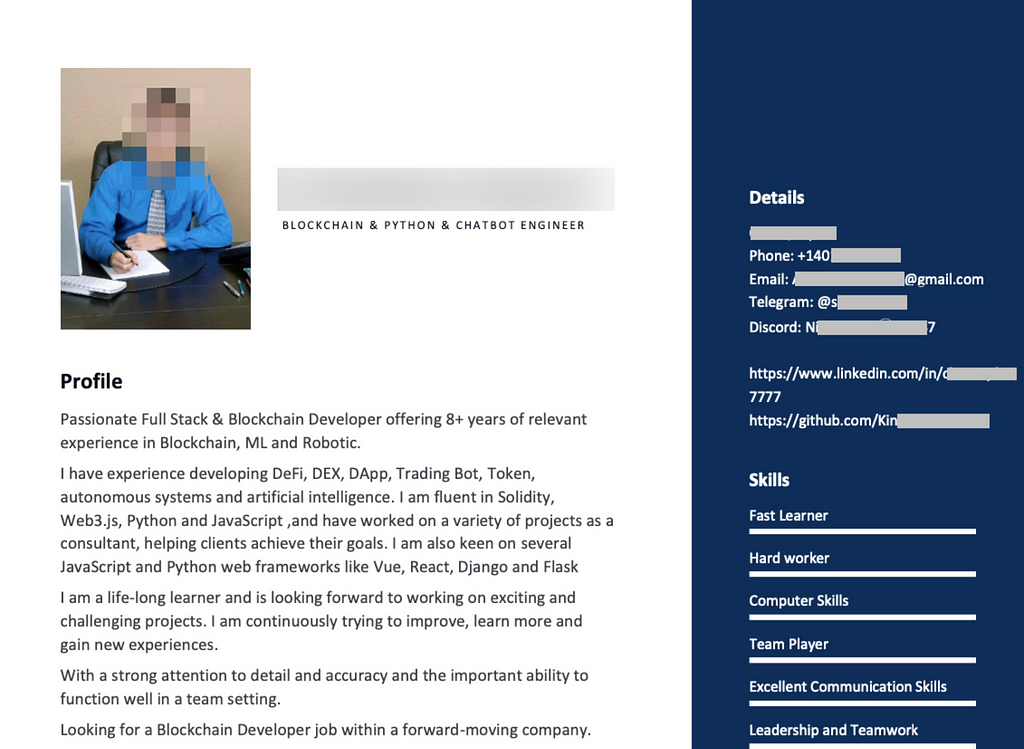
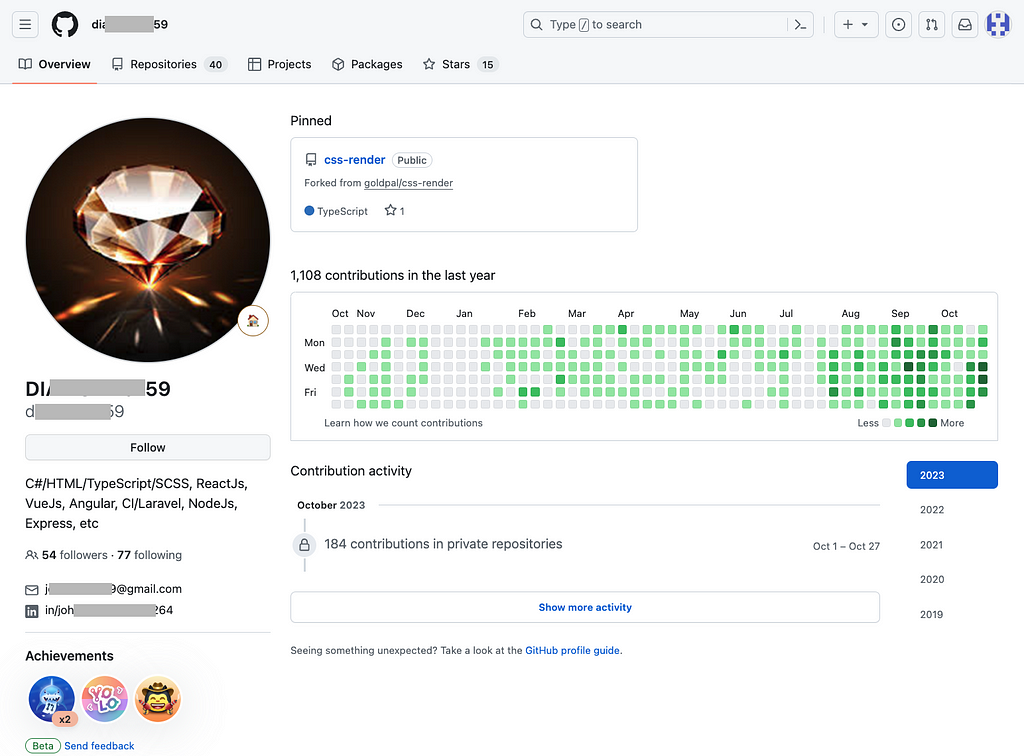 Wagemole Operation Proofs Collected by Unit 42 — Source: Unit 42
Wagemole Operation Proofs Collected by Unit 42 — Source: Unit 42First identified at the end of 2023 by Unit42, 2024 witnessed multiple cases targeting crypto actors.
According to an August report from crypto investigator ZachXBT, this campaign has already siphoned at least $7.7 million from crypto entities in just a few weeks.
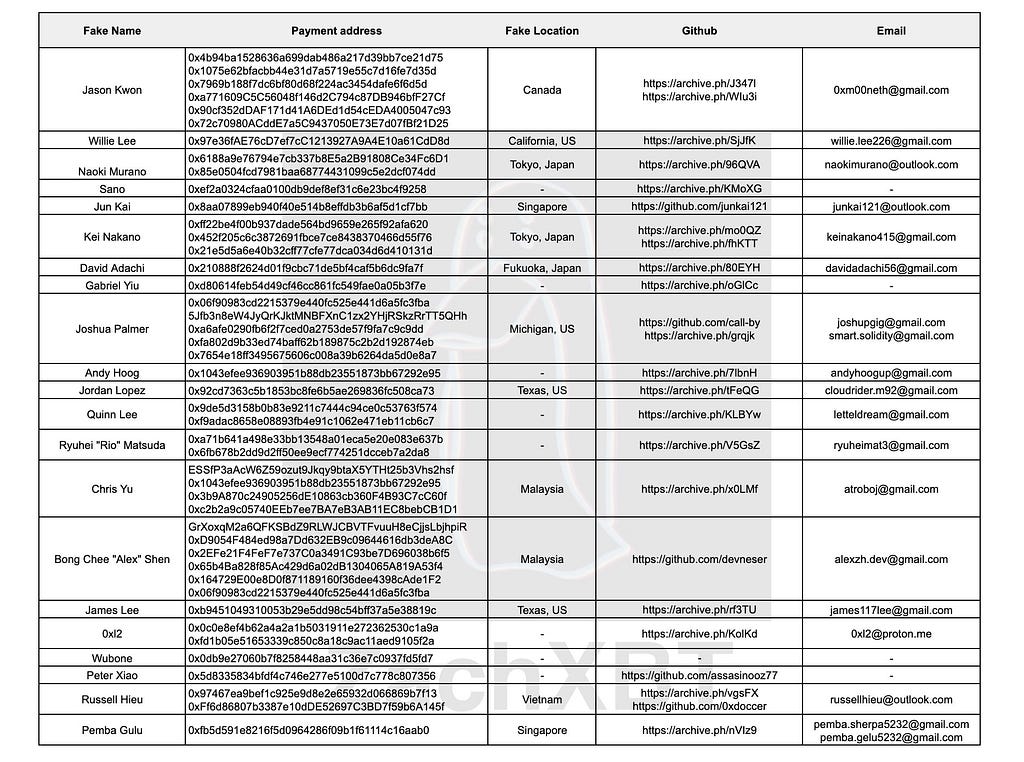
 Fake Employees Data — Source: ZachXBT
Fake Employees Data — Source: ZachXBTOn September 16th, the DeFi protocol Delta Prime fell victim to a private key exploit that cost them over $6 million. ZachXBT revealed that Delta Prime was among the infiltrated targets he had identified back in August. Delta Prime had informed him they had removed all the North Korean moles, but it seemed it was already too late, as the protocol had already been compromised.
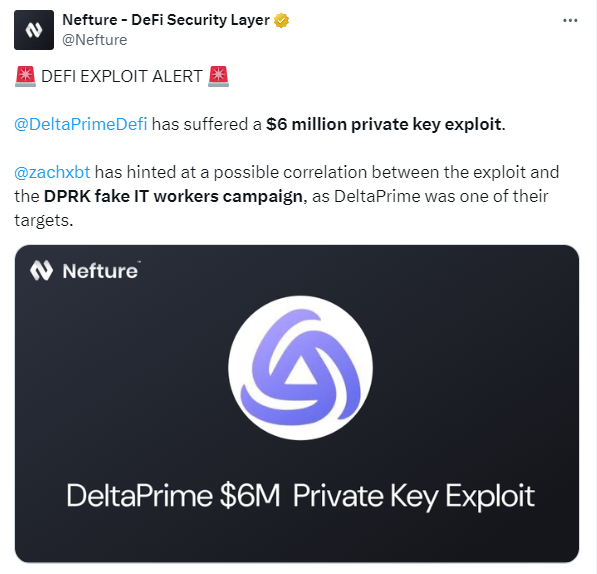 Source: Nefture
Source: NeftureAs of now, Operation Wagemole has not been formally traced back to the Lazarus Group. The extremely time-consuming nature of the operation, involving dozens, if not more than one hundred undercover agents, likely suggests that a unit specialized in such attacks has been established.
The Lazarus Group is just one of many North Korean threat actor sub-units targeting the cyber and crypto space. The Lazarus Group has focused on high-end, surgical attacks that do not involve the mobilization of agents for long periods of time, which makes it unlikely that they are behind the Wagemole attacks, but not impossible.
This is a subject we discussed at length in our in-depth report on the Lazarus Group: All You Need to Know About North Korean Crypto Hackers: The Lazarus Group.
So now, outside of the Lazarus Group (APT38) and sub-unit APT43, which specializes in laundering dirty crypto through clouds, it seems another North Korean threat targeting, in part, the crypto space has emerged.
Although the Lazarus Group may not have been the task force behind the Wagemole attacks, both of those social engineering relies single-handedly on the use of extremely sophisticated software developed, for most of them, by the Lazarus Group.
The past few months saw the Lazarus Group bringing their infiltration tools to an even higher standard, making their attack more funds-and-intel deadly than ever.
The Lazarus Group Enhanced Attack ToolsToo often, the Lazarus Group heists are downplayed, with some even questioning the use of the term ‘hacks.’ But hacks they are.
The social engineering aspect is only the first step — it’s the foot in the door if you will. That’s when the social engineering ends and the hacking begins, as seen in the CoinsPaid case.
They have a set of hacking tools, but one of them, reportedly used in the Contagious Interview by Unit 42, has a new enhanced iteration. Codename: BeaverTail.
How BeaverTail Operates —
BeaverTail’s core functionality revolves around the theft of sensitive information from compromised machines.
As an info stealer, DPRK threat actors have deployed BeaverTail in multiple campaigns aimed at ensnaring job seekers through various deceptive tactics.
Even when it was only “a JavaScript-based information stealer,” Beaver was already a powerful tool.
Once installed, BeaverTail performs initial reconnaissance on the infected system. It then downloads a secondary tool known as InvisibleFerret.
This secondary tool is a Python-based backdoor that significantly enhances BeaverTail’s capabilities. InvisibleFerret includes features such as keylogging, data exfiltration, and remote control, allowing the malware to harvest a broad range of sensitive data.
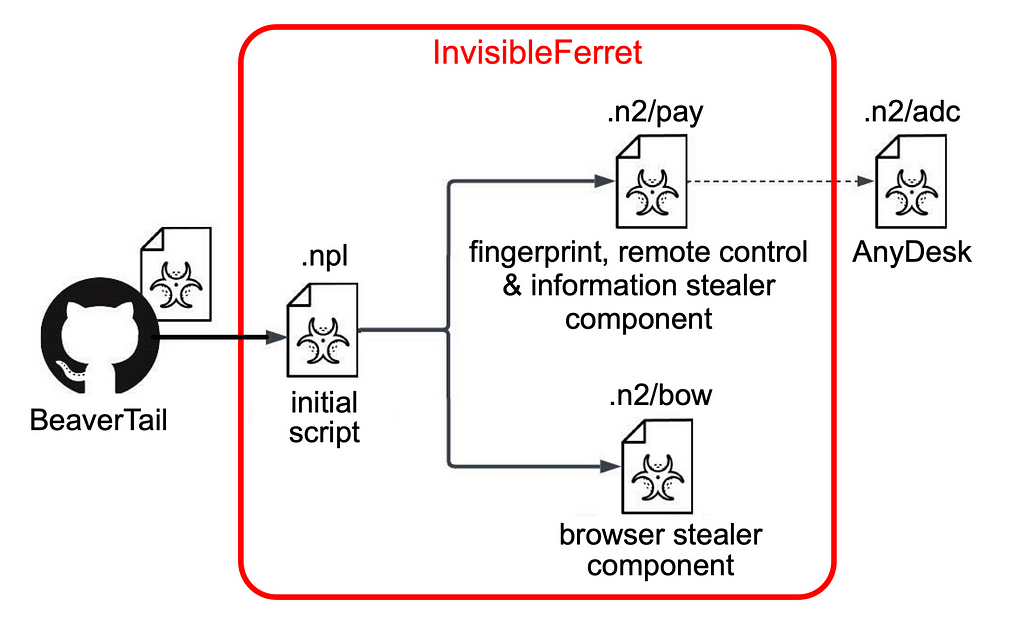 Source: Unit42
Source: Unit42The BeaverTail-InvisibleFerret integration allows the attackers to conduct more comprehensive and persistent attacks, increasing the overall impact of the malware.
Since its first iteration, BeaverTail has evolved into a more complex and dangerous threat.The malware now includes a native macOS variant designed to masquerade as legitimate software, such as MiroTalk, a video-conferencing application. This new iteration of BeaverTail was identified in July 2024.
The malware is adept at disguising itself as legitimate software, tricking users into downloading and executing it.
The trojanized version of MiroTalk mimics the legitimate video conferencing service while actually delivering the malware.
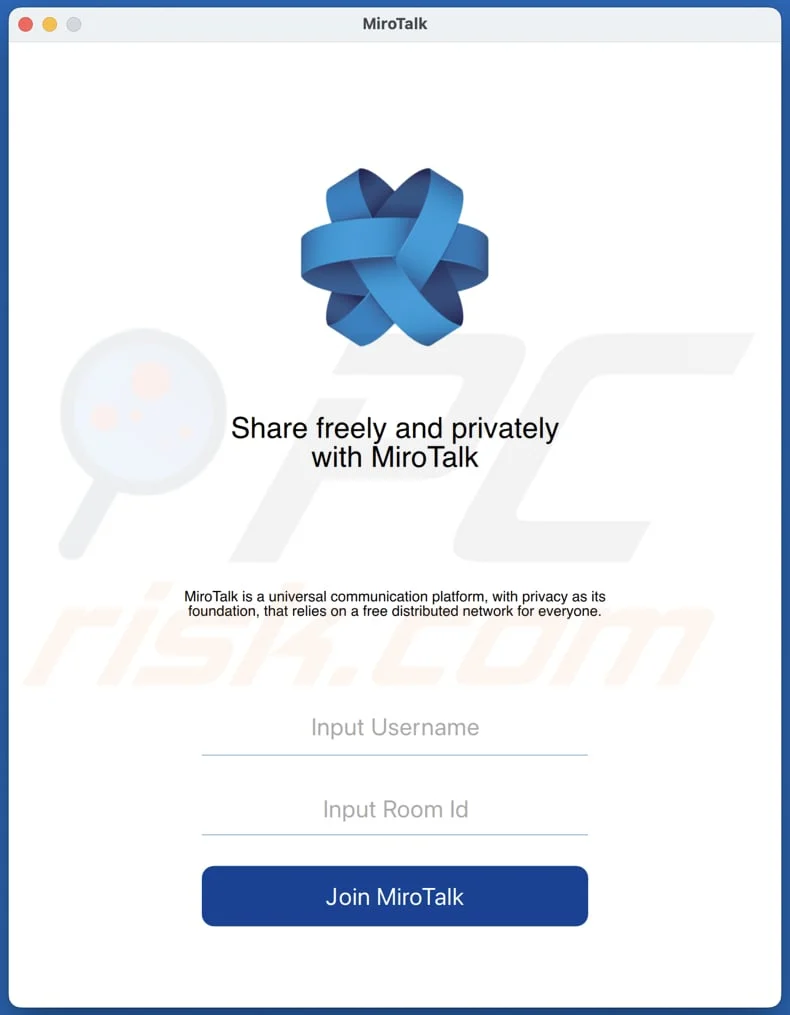
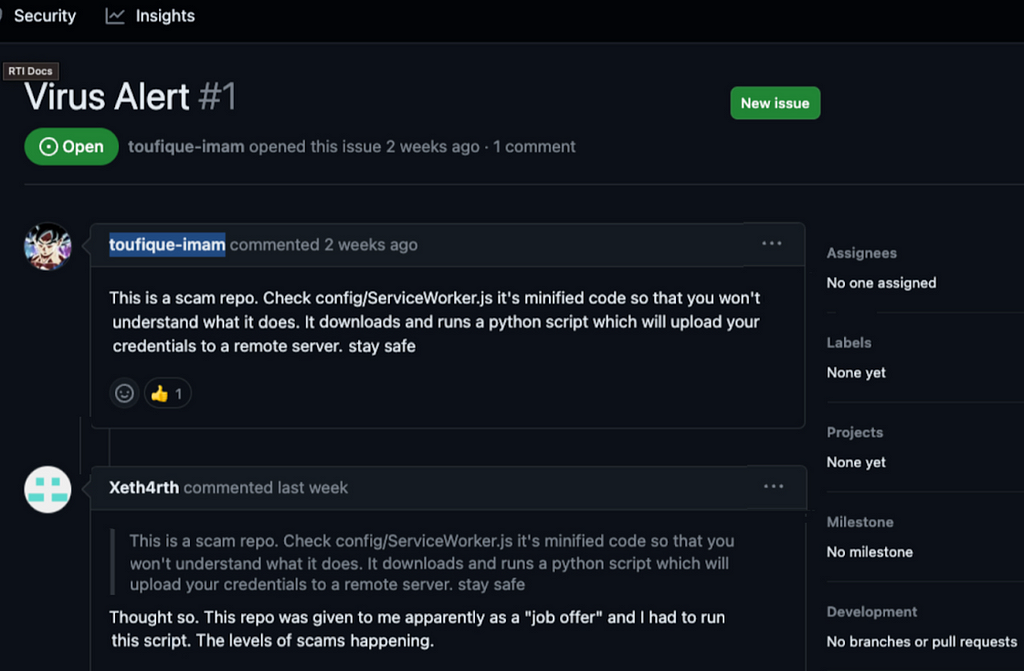 Image 1: Trojanized Version of MiroTalk — Image 2: Scam Repo Alert By Victims of Trojanized MiroTalk-BeaverTrail attack I Source: Unit42
Image 1: Trojanized Version of MiroTalk — Image 2: Scam Repo Alert By Victims of Trojanized MiroTalk-BeaverTrail attack I Source: Unit42Functionality and Features of macOS’ BeaverTail —
BeaverTail’s primary objective is to extract valuable information, particularly targeting cryptocurrency-related data. The malware focuses on capturing browser extension IDs for popular cryptocurrency wallets, paths to user browser data, and macOS keychain information. This data is crucial for cybercriminals seeking to compromise cryptocurrency assets.
The newer macOS variant of BeaverTail operates as a native Mach-O executable, offering a more stealthy and efficient means of infection compared to its JavaScript predecessor.
The malware’s behavior includes communicating with specific API endpoints, indicative of its sophisticated data exfiltration and command-and-control operations.
The evolution from the old JavaScript-based BeaverTail to the new native versions represents a significant advancement in the malware’s capabilities and sophistication.
1.Old BeaverTail (JavaScript-Based) — The earlier iteration of BeaverTail was distributed primarily through JavaScript files embedded within Node Package Manager (NPM) packages.
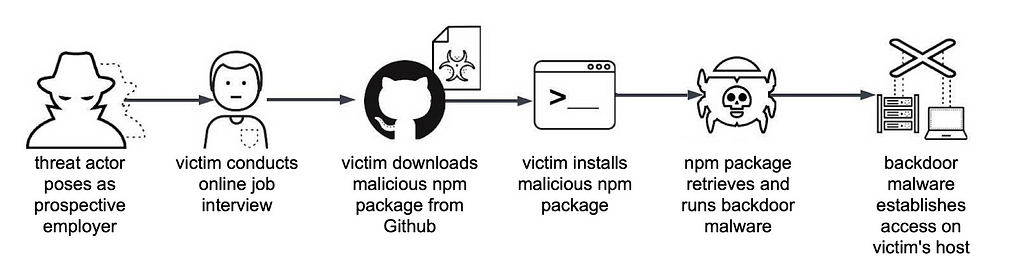
This version used obfuscated JavaScript to evade detection, operating within the constraints of a web environment.
It was designed to target browsers and extract information related to cryptocurrency wallets and other sensitive data.
The use of JavaScript made it somewhat less efficient and more easily detectable compared to compiled executables.
2.New BeaverTail — The newer version of BeaverTail is a native executable tailored for a specific operating system: macOS. For macOS, the malware is now a Mach-O executable.
These native versions offer several advantages over the JavaScript variant, including deeper system integration, more efficient execution, and improved stealth.
Native executables can bypass some of the security mechanisms designed to protect against JavaScript-based threats and offer more robust capabilities for data exfiltration and system control.
But even worse, just a few weeks ago, Group-IB Threat Intelligence uncovered that a Windows variant of the malware, similar to the macOS version, is now also active.The New Windows Version of BeaverTail —
The Windows variant of BeaverTail represents a significant development in the malware’s evolution. Building on the capabilities of its predecessors, this new version extends BeaverTail’s reach beyond macOS, targeting Windows operating systems with sophisticated tactics.
Deployment and Operation
The Windows version, identified as FCCCall.exe and mimicking the legitimate “FreeConferenceCall.com” app, was part of a campaign observed by Group-IB Threat Intelligence between late July and early August 2024. This campaign is similar to the earlier operation that trojanized the MiroTalk application.
It also operates similarly to its macOS counterpart, performing functions such as data exfiltration and payload execution. This version also leverages the InvisibleFerret backdoor to enhance its capabilities, including keylogging and remote access.
Expansion of Targeting and Scope
The introduction of the Windows version and the expansion of targeting capabilities signify a strategic evolution in BeaverTail’s operations. The malware now targets a broader range of browser extensions and cryptocurrency wallets, including new entries such as Kaikas, Rabby, Argent X, and Exodus web3, as reported by Group-IB Threat Intelligence.
The differences in deployment and functionality between the two versions highlight BeaverTail’s versatility and the attackers’ ability to adapt their tactics to various platforms. Each version is optimized for its target environment, enhancing the malware’s effectiveness and making detection more challenging.
This expansion shows that BeaverTail’s operators are intent on targeting a broader spectrum of victims’ cryptocurrency assets. The widened scope highlights the malware’s adaptability and the attackers’ determination to maximize their data theft operations, now extending their reach from small retail investors to large-scale “whale” targets.
We can expect more diverse and intensified exploit campaigns aimed at mapping the entire crypto ecosystem and exploiting every vulnerability — whether existing or newly created (by them) — to siphon off every available fund.
This development intensifies the danger posed by the Lazarus Group and other North Korean threat actors behind these heist operations, further destabilizing the already vulnerable crypto ecosystem — one of the last threats it can afford to face.
Crypto Money Laundering: The Rise of the Huione Group
Money laundering is the most important industry within crypto crimes. Unlike traditional criminal setups, where ill-gotten funds are in fiat and can be mobilized immediately, crypto crimes and cybercrimes involving cryptocurrencies must cash out in order to truly profit.
In our H1 2024 report, we tackled new adoption practices in money laundering strategies.
Q3 brought staggering news about the rise of a new powerful money laundering tool, its symbiotic connection with the pig butchering industry, and its adoption by important crypto criminal players.
The Huione Group: An Unstoppable Money Laundering MachineA new money laundering tool, Huione, has surfaced in the crypto space, connected to the $64 billion pig butchering scam and the Cambodian ruling elite. The success of this scam necessitated a dedicated money laundering ecosystem, attracting interest from North Korea’s Lazarus Group and other cybercriminals.
Investigations by Elliptic, the UN Office on Drugs and Crime, and Radio Free Asia revealed that Huione is tied to the cousin of the Cambodian prime minister, suggesting a deep-rooted connection.
A few weeks ago, blockchain security firm Elliptic revealed findings from their investigation into pig butchering scams that led them to Huione Guarantee (汇旺担保), a branch of the Cambodian conglomerate Huione Group.
Huione Guarantee has quickly become a hub for money laundering and illicit trading, particularly for pig butchering schemes in Southeast Asia. It operates as an escrow service within a Chinese-language marketplace consisting of thousands of instant messaging app channels managed by individual merchants. They claim their role as a guarantor helps combat fraud.
But can fraud truly be prevented if you do not “participate in nor understand the specific business of customers,” nor can you verify or guarantee the “origin of funds or goods?”
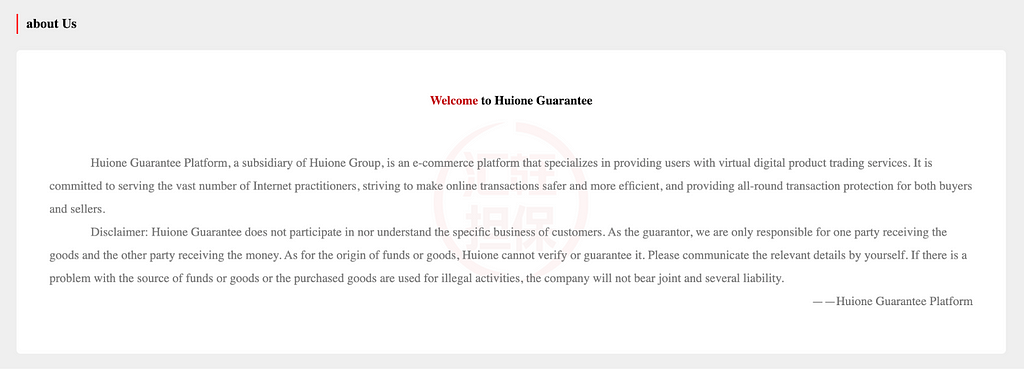 Source: Elliptic
Source: EllipticA closer examination of Huione Guarantee’s seemingly legitimate facade revealed that, according to Elliptic, it had become a criminal haven for pig butchering schemes. Established in 2021, when the pig butchering business was already entrenched in Cambodia, Huione “merchants” offer technology, data, money laundering services, and logistical support specifically for cyber scam operators.
Their offerings include:
- Development services to create fraudulent crypto investment websites that appear legitimate to victims of pig butchering.
- AI deepfake software to impersonate identities and ensnare targets in elaborate traps.
- Targeted data, including worth and contact details, to pursue high-value victims.
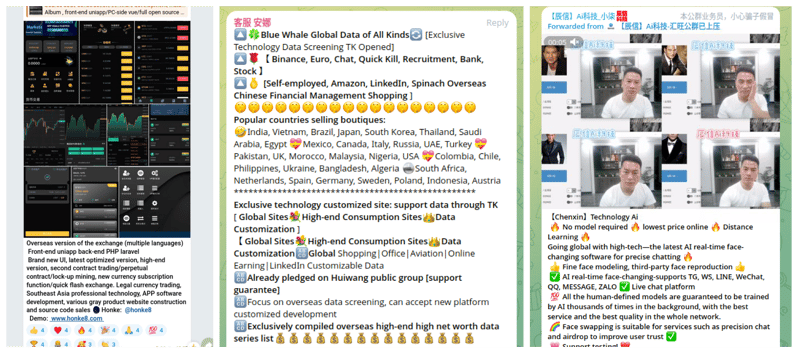 “Huione Guarantee merchants offering web development of cryptocurrency investment sites of the type used in pig butchering scams (left), personal data of individuals around the world for targeting by scammers (middle), and AI face-changing software advertised for use in scams (right).” — Source: Elliptic
“Huione Guarantee merchants offering web development of cryptocurrency investment sites of the type used in pig butchering scams (left), personal data of individuals around the world for targeting by scammers (middle), and AI face-changing software advertised for use in scams (right).” — Source: Elliptic- Torture equipment. As detailed in our report on pig butchering scams, most of the pig-butchering “scammers” are actually victims of cyber-enslavement, forced under duress and torture to carry out scams globally while imprisoned in industrial-scale scam centers. Huione merchants also provide various torture tools, including tear gas, electric batons, and electronic shackles, according to Elliptic. These items are used to exert control over primary victims, who are derogatorily referred to as “dogs” by both merchants and scam centers.
 “Advertisements on Huione Guarantee for electric shock shackles (left) and electric batons (right), which the merchants suggest are to be used on scam compound workers.” — Source: Elliptic
“Advertisements on Huione Guarantee for electric shock shackles (left) and electric batons (right), which the merchants suggest are to be used on scam compound workers.” — Source: EllipticThe most significant aspect of the Huione Guarantee, both in terms of the volume of dealings and merchant activity and its relevance to the crypto criminal landscape, is money laundering.
According to Elliptic, the platform openly offers money laundering services, including accepting payments from global victims, transferring funds across borders, and converting them to cash, stablecoins, and Chinese payment apps.
Money launderers also openly discuss which types of fraud proceeds they are willing to handle based on the perceived risk of having their funds frozen.
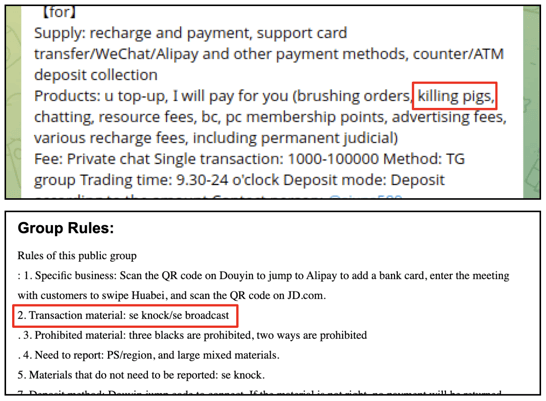 “(Top) a Huione Guarantee merchant offers to launder proceeds of fraud, including pig butchering scams. (Bottom) another merchant specializes in the laundering of sextortion scams (“se敲” — translated here as “se knock”)” — Source: Elliptic
“(Top) a Huione Guarantee merchant offers to launder proceeds of fraud, including pig butchering scams. (Bottom) another merchant specializes in the laundering of sextortion scams (“se敲” — translated here as “se knock”)” — Source: EllipticIt’s no surprise that money laundering thrives on the Huione Guarantee platform, as pig butchering scams alone generate at least $64 billion annually for criminal organizations, according to the 2024 “Transnational Crime in Southeast Asia Report” by the United Nations Office on Drugs and Crime. Cambodia, along with Laos and Myanmar, is at the center of this activity.
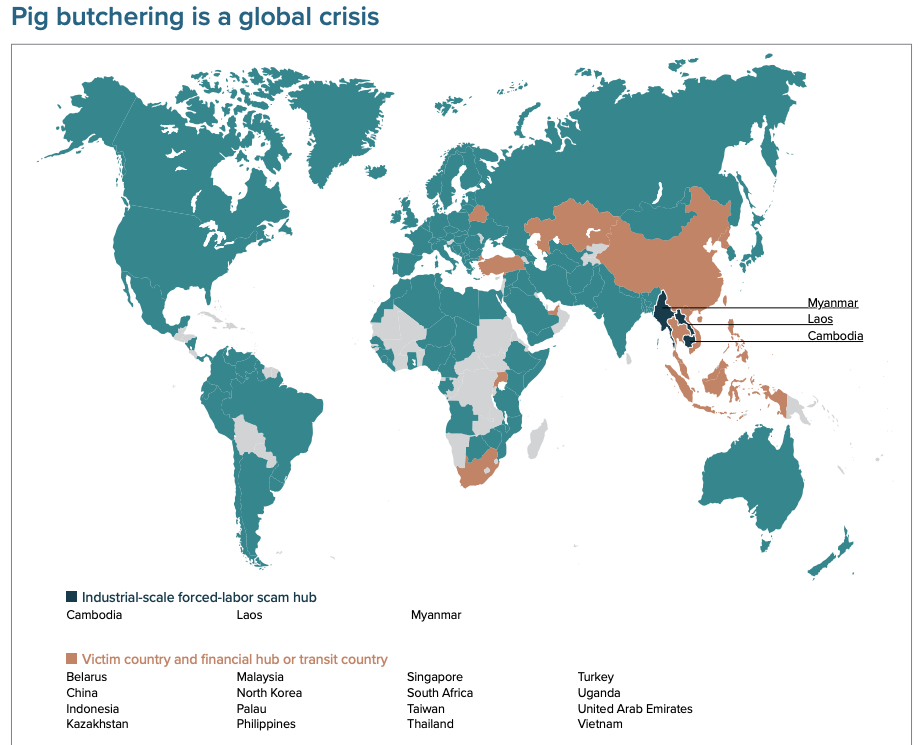 Source: Transnational Crime in Southeast Asia Report by UNODC
Source: Transnational Crime in Southeast Asia Report by UNODC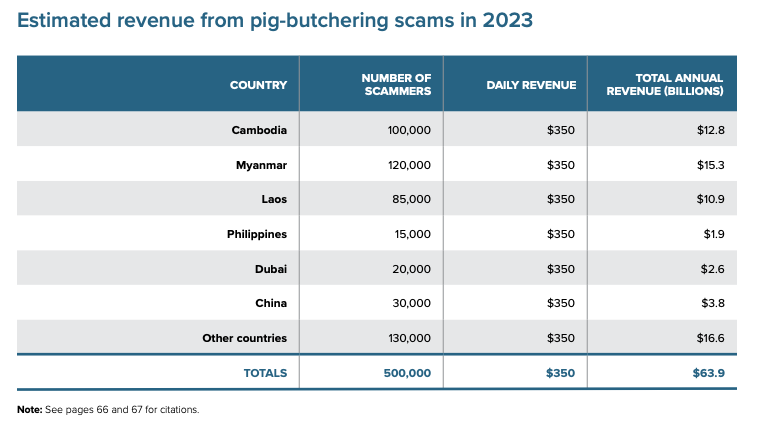 Source: Transnational Crime in Southeast Asia Report by UNODC
Source: Transnational Crime in Southeast Asia Report by UNODCThe cornerstone of the pig butchering scheme and associated money laundering activities is the USDT stablecoin, which is the preferred currency on the Huione Guarantee platform. Payments are primarily accepted in USDT, though some fiat transfers are allowed.
According to the UNODC report, USDT is favored for regional cyber fraud and money laundering due to its stability, ease of use, anonymity, and low transaction fees. However, criminals’ mistaken belief that USDT is difficult to trace has often led to their downfall. By tracking USDT flows, Elliptic uncovered that crypto wallets linked to Huione Guarantee and its merchants had accumulated at least $11 billion since 2021.
Based on Elliptic’s analysis of thousands of messages and months of investigation, Huione Guarantee predominantly functions as an illicit marketplace, with most, if not all, of the $11 billion tied to illegal activities, primarily from pig butchering scams.
 “Value of USDT received by cryptocurrency wallets known to be used by Huione Guarantee and its merchants. These figures should be considered as lower bounds of the true volume of transactions on the platform.” — Source: Elliptic
“Value of USDT received by cryptocurrency wallets known to be used by Huione Guarantee and its merchants. These figures should be considered as lower bounds of the true volume of transactions on the platform.” — Source: EllipticIf Huione Guarantee ever prevented fraud, well, it seems it was to prevent its criminal clients from one-upping each other and to forcefully ensure, as an escrow service, that there would be honor among thieves.
They have been so good at making good on their promise of “providing all-around transaction protection for both buyers and sellers” that it has caught the attention of malicious actors outside of Southeast Asia, across borders, including the infamous North Korean state-sponsored group Lazarus.
Huione, A New Money Laundering Tool for The Lazarus GroupFive days after Elliptic’s report on Huione Guarantee, crypto investigator ZachXBT revealed a connection between Huione and the Lazarus Group.
One significant exploit occurred on May 31, 2024, when the Japanese exchange DMM Bitcoin suffered a private key exploit, resulting in a loss of $308 million — marking the largest crypto heist since the FTX hack in November 2022.
ZachXBT traced the money laundering patterns back to the Lazarus Group, which used Huione Guarantee to launder over $35 million in early July 2024. This discovery aligns with findings from UNODC investigators, who had previously identified the Lazarus Group operating a money laundering pivot to Southeast Asia, sharing networks with fraudsters and drug traffickers.

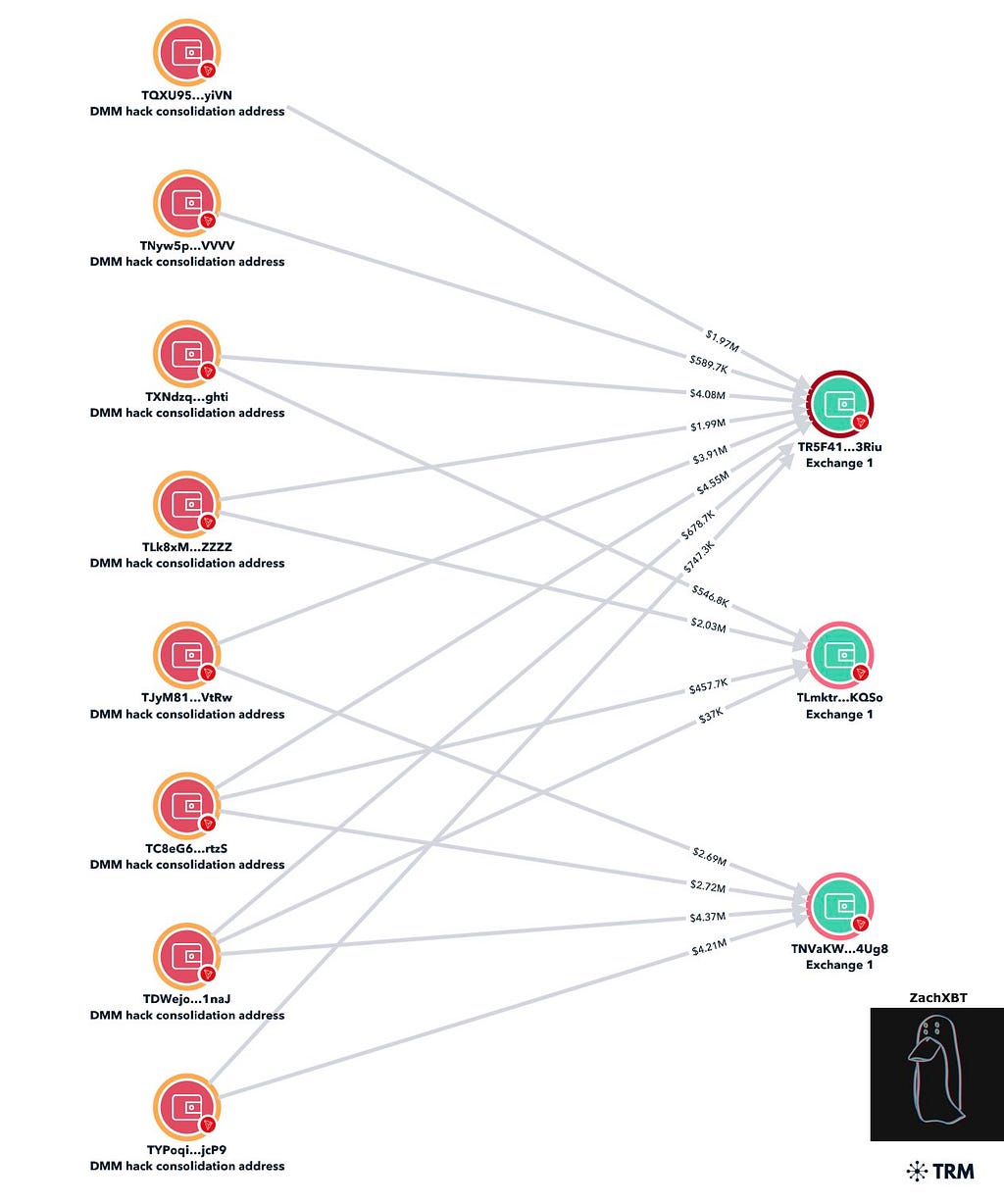 Source: ZachXBT
Source: ZachXBTThe day after ZachXBT’s findings, a Reuters report revealed that the FBI discovered the Lazarus Group laundered at least $150,000 through Huione Pay, another branch of Huione Guarantee, from the proceeds of three high-profile hacks in 2023, totaling over $200 million. TRM Labs noted that after these hacks, the group converted stolen funds to USDT on the Tron blockchain and sent them to various exchanges, including Huione Pay.
Comparing the $150,000 laundered through Huione with the $35 million laundered in July suggests that the Lazarus Group was testing Huione as a new laundering route.
Their subsequent large-scale return indicates a successful trial, solidifying Huione’s role in their money laundering operations.
The Lazarus Group’s involvement with the Huione Group triggered law enforcement’s attention. The US, in particular, has been aggressively targeting North Korea’s alleged crypto-criminal activities and has taken down or brought to heel every entity found to be actively laundering money, such as Tornado Cash and Samurai Wallet.
On the one hand, the Lazarus Group brought in millions and, as a crypto money laundering trendsetter, will attract a flock of new users to the Huione Group. On the other hand, they have brought increased international scrutiny to their operations.
Will the Lazarus Group’s involvement with Huione be a financial blessing or instead provoke Huione’s downfall?
One thing is almost certain: if the Lazarus Group continues using the Huione Group, and Huione does nothing about it, it could ultimately trigger a political battle between the US and Cambodia.
Mimicking Double Hack Incidents: Bad Habits and Unforgivable Errors
Threat actors lurking 24/7, devising extremely sophisticated attacks and successfully employing them, even bypassing the most arduous security measures built over years of blockchain security experience and guaranteed by the vigilance of contracted blockchain security companies, is not what a typical crypto hack looks like.
It’s the radical opposite. Most of these hacks happen as the byproduct of sheer negligence — aka not security testing or auditing upgraded contracts. This leaves glaring vulnerabilities for any crypto criminal bystander, who will, of course, come and help themselves to the free buffet.
The free buffet offers anywhere from tens of thousands to dozens of millions of dollars.
But, as with everything, there’s nuance. There’s a difference — or a decency gap — between a victimized, cheap, negligent protocol and those that are practically inviting an attack at this point.
Such was the case with two DeFi protocols during the summer of 2024.
The Li.Fi CaseFive days before the attack, on July 16th, 2024, the LiFi team deployed the GasZipFacet contract without auditing it.
The newly deployed contract contained an arbitrary call vulnerability in the depositToGasZipERC20()function, which allowed unauthorized transactions and was exploited by the attacker.
On July 16th, 2024, our risk detection system immediately identified the attack, and we promptly alerted our users and the Web3 community.
All Li.Fi users who had given infinite approvals for specific LiFi contract addresses suddenly found themselves at risk of being siphoned and siphoned they were, as the hacker made off with $11.6 million. The bounty could have been even higher if not for the swift response of the blockchain security ecosystem, which promptly alerted the crypto community.
The worst part? This could have been entirely avoided if — just if — whatever skeleton blockchain security body Li.Fi had learned their lesson when the exact same thing happened two years earlier.
According to blockchain security firm Peckshield, in March 2022, the Li.Fi Protocol had already lost $600,000 under similar circumstances. In that instance, their contract also suffered from an arbitrary call vulnerability, which was exploited through the internal swap()function, ultimately siphoning funds from users who had given infinite approvals.
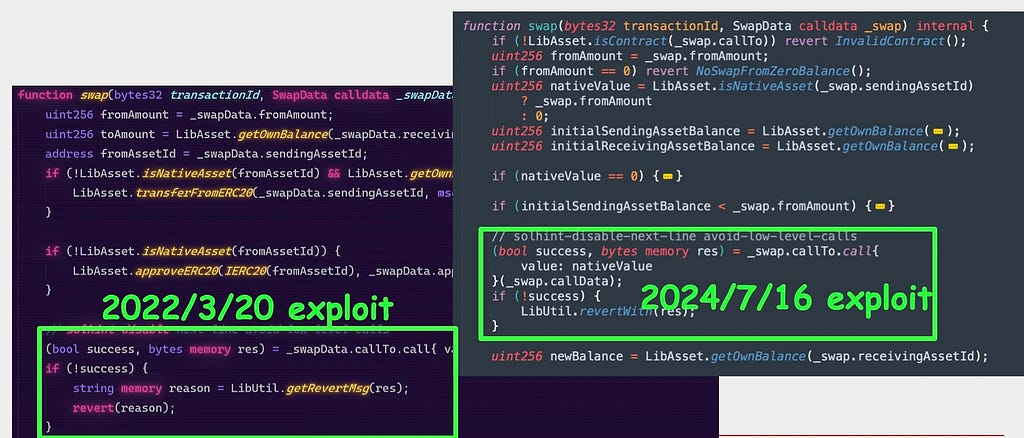 Li.Fi March 2022 & July 2024 Hacks — Source: Peckshield
Li.Fi March 2022 & July 2024 Hacks — Source: PeckshieldHowever, all this could have simply been avoided by not making risky, unaudited upgrades to an existing protocol contract and entirely forgetting known vulnerabilities in the first place.
The Onyx CaseAlthough Li.Fi was bad, somehow, the Onyx case is worse.
At the beginning of September, Onyx launched a new VUSD market.
On September 26th, an attacker took out a 2,000 ETH flash loan from Balancer, depositing 1,999.5 ETH into a contract and 0.5 ETH into a malicious contract.
According to Hacken, they then repeatedly minted and redeemed tiny amounts of oETH (0.00000001) 56 times, manipulating the asset’s exchange rate.
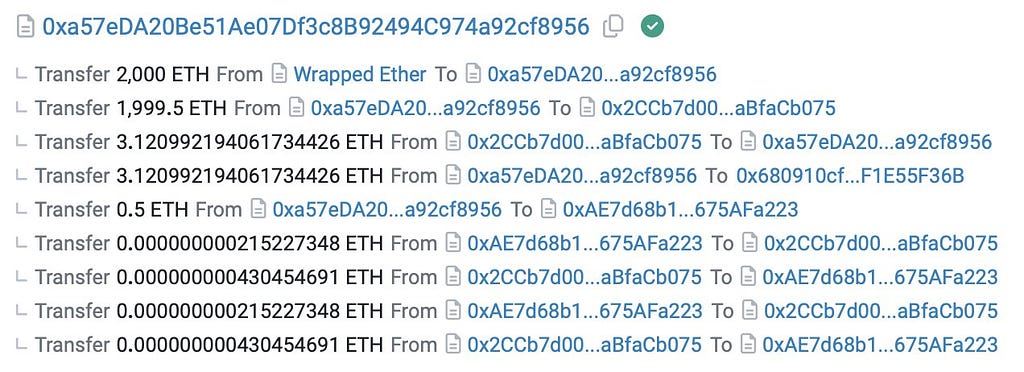 Onyx Hack Attack — Source: Hacken
Onyx Hack Attack — Source: HackenThey even succeded in inflating the self-liquidation reward by exploiting a vulnerability in the NFTLiquidation contract, which didn’t check user input correctly. No security audit has been recorded since their January 2022 audit by Certik, despite numerous updates and implementation.
In total, the attacker was able to siphon $3,8 million.
This was a hack that could have been avoided, as they went through nearly the same scenario (minus the NFT liquidation exploit) less than a year earlier, in November 2023, when they lost $2.1 million under identical circumstances.
However, this time, the attack occurred just after Onyx had approved a brand-new lending market for PEPE.
The November 2023 hack was already inexcusable, as 2023 had been marked by multiple high-profile cases exploiting the same vulnerability.
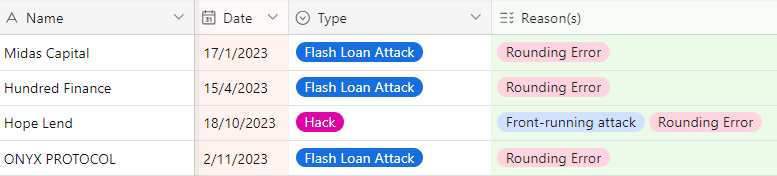 Crypto Crime Database — Source: Nefture
Crypto Crime Database — Source: NeftureThese exploits all targeted a rounding error in Compound v2’s code. The Compound v2 fork has a known issue with decimal precision in markets with low liquidity, rounding errors allowing attackers to manipulate empty markets, causing the exchange rate to break down in such conditions. This exploit is also known as an “empty pool attack.”
Newly launched markets and unfavorable market conditions that create empty pools make for perfect targets. A simple step to mitigate an “empty pool attack” is to mint and burn a low amount of tokens, preventing the market from becoming empty. The total supply should never hit zero.
A very simple step that Onyx didn’t even care to implement the first time, despite being aware of the risk, nor after being hit by a multi-million dollar attack.
Q3 2024 Scam Landscape: The Unstoppable Crypto Phishing Machine
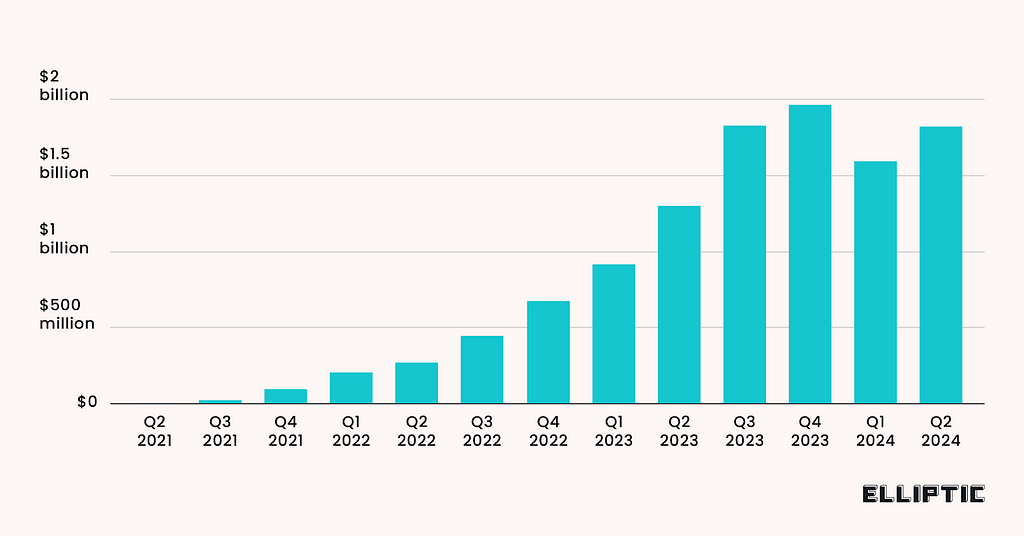
The 2024 phishing figures are vertigo-inducing, especially in this last quarter. More than $405 million was lost to phishing attacks in the summer of 2024, accounting for almost half of what has been stolen this year: $813 million, of which $91 million has been recovered.
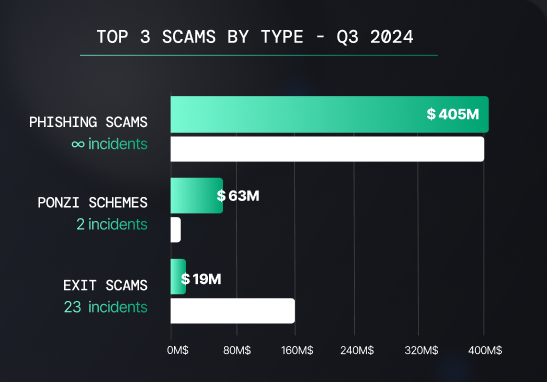 Top 3 Scams By Type, Q3 2024 — Source: Nefture
Top 3 Scams By Type, Q3 2024 — Source: NefturePhishing has been absolutely dominating the crypto fraudscape this quarter.
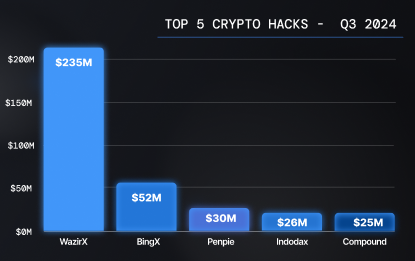
With Q3 witnessing the biggest phishing heist in crypto history, it marks the second-largest crypto crime of the year, following the $308 million DMM Bitcoin exploit, which involved $243 million stolen from a single victim.
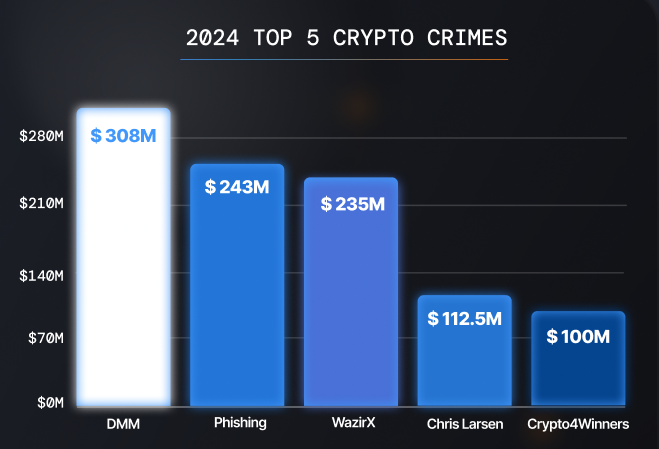 2024 TOP 5 Crypto Crimes — Source: Nefture
2024 TOP 5 Crypto Crimes — Source: NeftureThat’s why, in today’s report, we decided to focus on an intrinsic breakdown of the phishing scene, its key players, and their tools.
$243 Million Stolen in the Biggest Social Engineering Phishing Heist to Date
On August 19th, 2024, crypto sleuth ZachXBT took to Twitter to reveal that he had uncovered a suspicious transfer amounting to $238 million, with attempts to launder and cash out the funds through multiple centralized exchanges (CEXs). Rumors quickly swirled around the identity of the victim — was it an individual, a hedge fund, or a CEX? And how was the heist carried out: through a private key exploit, phishing, or both?
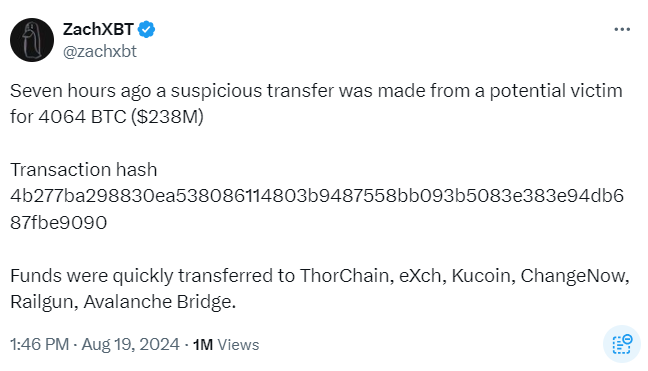
For a long time, little was known about the case, except for two updates from ZachXBT, which reported two successful attempts to freeze the stolen funds — by Firn Protocol and NonKYC — totaling around $500,000. Barely a drop in the bucket.
One month, jour pour jour, after the $238 million attack, ZachXBT took again to Twitter to reveal the full story behind it.
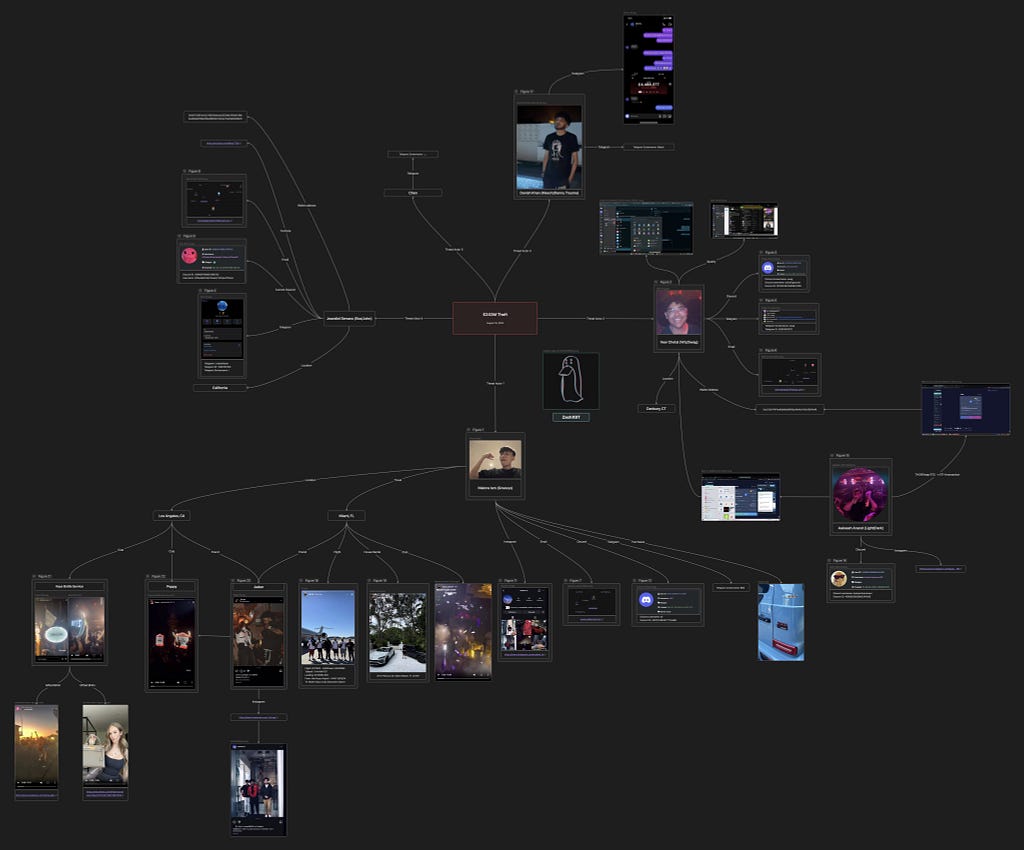 ZachXBT’s Investigation Mapping — Source: ZachXBT
ZachXBT’s Investigation Mapping — Source: ZachXBTThe heist was a “highly sophisticated social engineering attack,” a phishing scam that targeted a single individual. The victim was a creditor of the defunct crypto trading firm Genesis.
On the day of the attack, he received a call from a spoofed number, with the scammers posing as Google Support to compromise his personal accounts, according to ZachXBT’s investigation. Shortly after, the victim was contacted again, this time by the scammers posing as Gemini support. They informed him that his Gemini account had been hacked and instructed him to reset his 2FA and transfer funds from his Gemini account.
After much persuasion, the victim used AnyDesk to share his screen, allowing the scammers to access and leak his private keys from his Bitcoin Core.
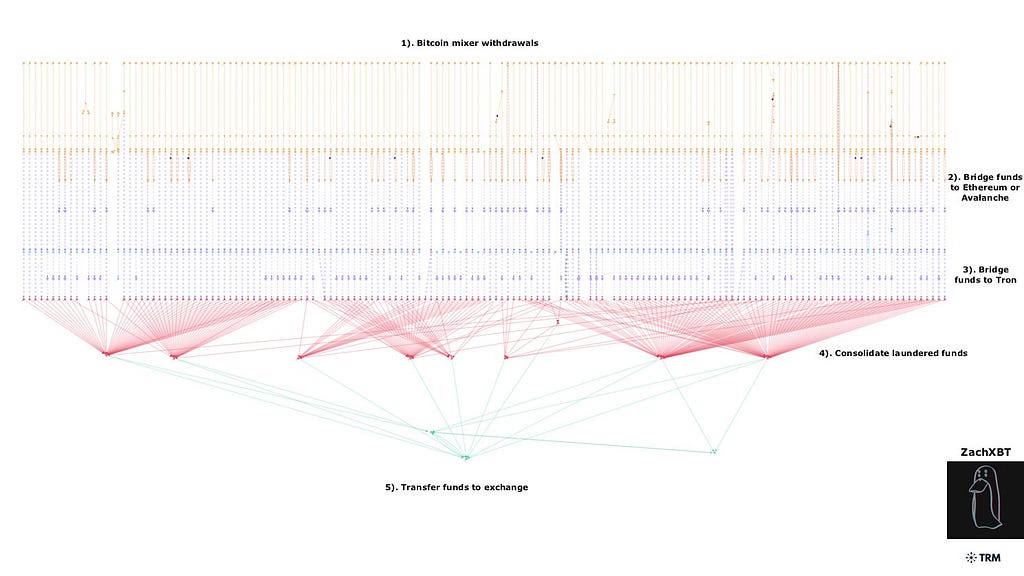
His attackers successfully stole $243 million and immediately attempted to disperse the funds across multiple wallets before transferring them to over 15 exchanges, according to ZachXBT’s research. The stolen assets were rapidly swapped between Bitcoin, Litecoin, Ethereum, and Monero in an effort to obscure the trail.
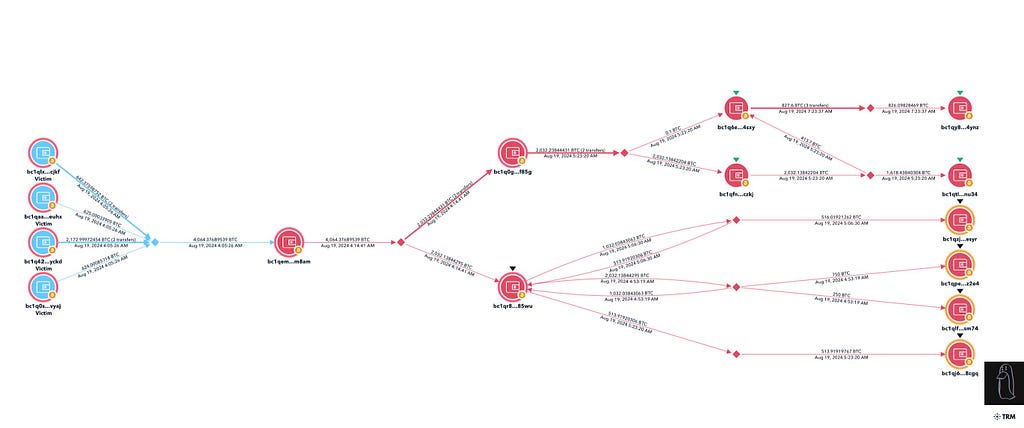 Initial Exploit Tracing by ZachXBT- Source: ZachXBT
Initial Exploit Tracing by ZachXBT- Source: ZachXBTUnfortunately for them, but fortunately for the victims, they were neither thorough during their attack nor in their attempt to escape. This lack of diligence allowed ZachXBT to trace the phishing attack back to three main perpetrators and their accomplices.
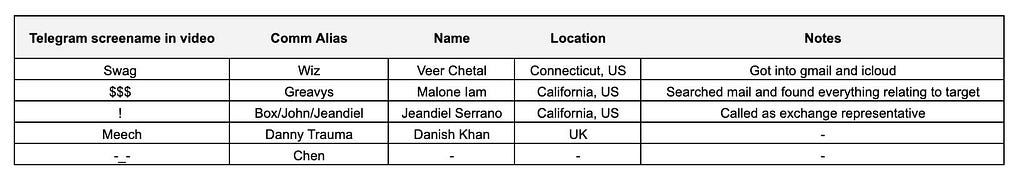 Suspect List Established by ZachXBT — Source: ZachXBT
Suspect List Established by ZachXBT — Source: ZachXBTOne of the many blunders they committed was revealing two of their names to the victim during the screenshare.
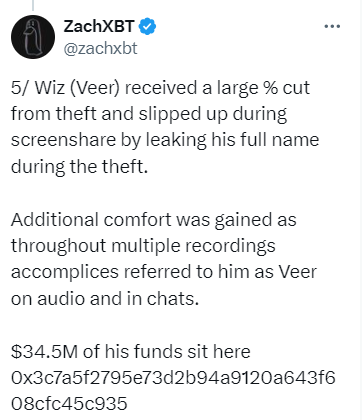
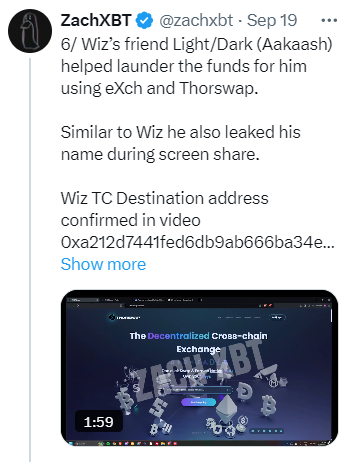 Source: ZachXBT Twitter
Source: ZachXBT TwitterThe other mistakes relate to their money laundering techniques. Although the attackers converted most of the stolen funds to Monero, ZachXBT discovered that two of them accidentally mixed stolen and clean funds by reusing a deposit address. One attacker, while sharing his screen, also revealed an address he used to purchase designer clothes, which was linked to millions in stolen money.
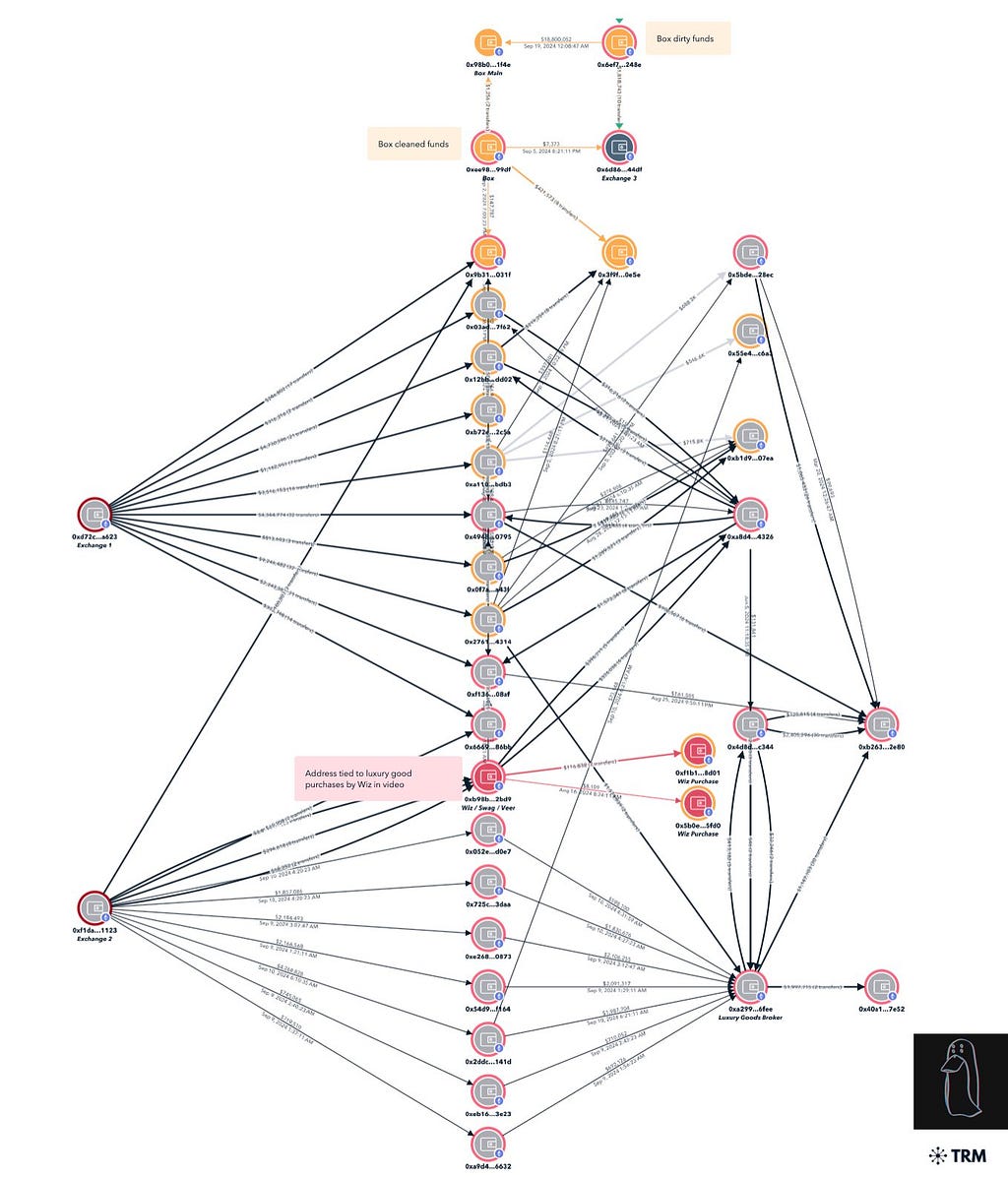 Tracing of Badly Laundered Funds by ZachXBT — Source: ZachXBT Twitter
Tracing of Badly Laundered Funds by ZachXBT — Source: ZachXBT TwitterMost of them had left enough trails on social media — or their exes did — for their full identities to be ultimately revealed during ZachXBT’s investigation. ZachXBT, alongside the Binance security team, Zero Shadow, and CryptoForensic Investigators, was able to further freeze $9 million.
The day before ZachXBT published his findings, Box (Jeandiel Serrano, 21) and Greavys (Malone Lam, 20) were arrested by the FBI and later indicted on September 19th.
 Malone Lam — Source: ZachXBT
Malone Lam — Source: ZachXBTPhishing through social engineering has been at the heart of many bountiful crypto heists, one of them extremely sophisticated, almost succeeding in wiping out $125 million from a single individual, as we recounted previously in Story of an Almost $100M Crypto Heist.
Story of an Almost $100M Crypto Heist
Although they remain impressive in their approach and the size of their gains, social engineering is currently an infinitesimal part of the crypto phishing scene. At the center of the crypto phishing bulldozing machine are wallet drainers, offered as a scam-as-a-service and permit phishing.
Wallet Drainers as a Scam-as-a-Service: The Beating Heart of Crypto Phishing

The wallet drainer industry is breaking every record this year. In our 2023 crypto crime report, we hypothesized that 2024 would be an even more bountiful year for wallet drainers.
Unfortunately, this forecast was correct.
While it took the whole of 2023 to siphon an astronomical $295 million, it took barely six months in 2024 to break that record, totaling more than $314 million stolen from around 266,000 victims, according to blockchain security company ScamSniffer.
The wallet drainer industry can inflict that much damage because it is not an industry of 10 of thousands of crypto criminals all around the world coding their very own wallet drainers and attacking, it relies today almost entirely on entities who have developed wallet drainers as a scam-as-a-service.
These entities wear different names.
Deceitful ones like “Angel” or “Pink,” meme-like ones like “Monkey,” or very explicit ones like “Inferno.”
Wallet drainers, in short, put fraud at everyone’s fingertips.In the past, one needed to be blockchain-savvy to construct a tool capable of draining a victim’s wallet with just a couple of clicks. However, SaaS has dismantled this barrier by selling wallet drainer kits.
Now, anyone can create a flourishing crypto phishing scam business. In its simplest form, implementing a phishing scam requires only an “anonymous” website. A quick Google search will reveal numerous websites ready to help you create a phishing site in less than ten steps. But nowadays, SAAS even offers a ready-to-scam website as a bonus.
The scam, most of the time, only requires a crude landing page. These are the standard for crypto scams, as many legitimate actors also use landing pages for giveaways, airdrops, or mints. The final step is to hide your drainer behind a “claim your airdrop” button or something similar, and voilà. That’s how, schematically, your average Joe can transform into a high-caliber crypto fraudster.
Now, let’s rewind a bit.
How does one come by a crypto wallet drainer kit?
As for everything scammy under the Milky Way’s sun, you will find it on Telegram. Telegram, aptly named the “Scammers Paradise,” is where the crews behind those crypto phishing kits openly sell them to all and asundry.
 Ad from Inferno Drainer on Telegram — Source: Group IB
Ad from Inferno Drainer on Telegram — Source: Group IBThe SAAS’s Business Model — 🚩
Pink Drainer, Angel Drainer, Inferno Drainer, and the like seem to have adopted the same business model.
They offer to individuals and phishing teams that allow them to drain crypto wallets on a turnkey basis for an initial hefty deposit and claim a 20–30% cut of the future phishing loot.
In blockchain security firm Slowmist’s report on Angel Drainer, it was revealed that it demanded from its “customers” a $40,000 deposit along with a 20% fee justified by the wholesome phishing service offered by Angel Drainer like automatic site cloning tool with linked drainer, multiple chains supports,…
As illustrated by this Angel Drainer’s “ad”:
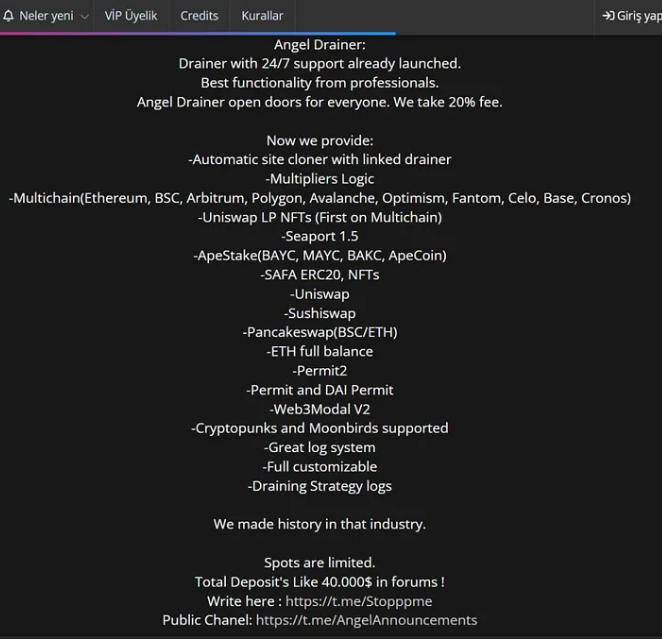 Source: Slowmist
Source: SlowmistAccording to Scam Sniffer report, in 2023, their drainer fees allowed those crypto SAAS to bank in at least $47 million. We can guess they have already banked in even more.
One must admit that’s quite a genius criminal plan.
The masterminds behind these drainers need to do absolutely nothing to rake in the cash.
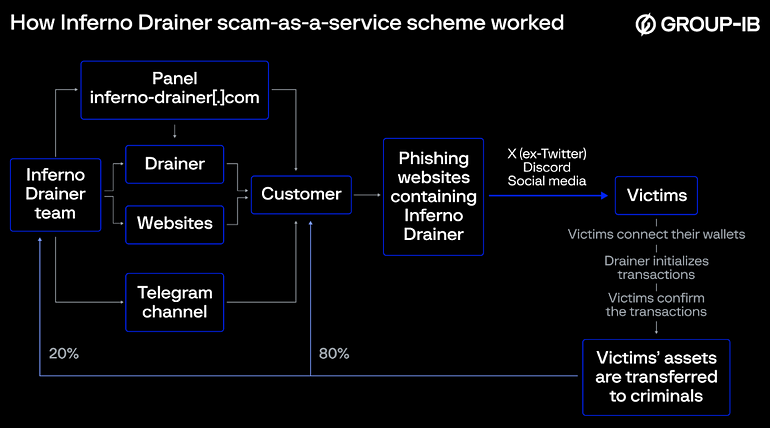 Detailed overview of Inferno Drainer’s workflow — Source: Group IB
Detailed overview of Inferno Drainer’s workflow — Source: Group IBThey never endanger their own safety and anonymity, while their customers are the ones investing time in mounting and running sometimes very expensive phishing scam campaigns and taking the risk of being exposed.
An Ever-Changing Landscape But A Persistent Threat🚩Although crypto wallet drainers are extremely lucrative, the SAAS players are ever-changing.
One of the most well-known, if not the first, recorded SAAS crypto wallet drainers, Monkey Drainer, was active from August 2022 to February 28th, 2023.
After a $16 million successful run, made from more than 18,000 victims and a 30% cut, the Monkey Drainer crew closed up the shop after they were exposed by crypto-sleuth ZachXBT.
Probably trying to escape the spotlight, they announced their “retirement” with plenty of dramatic flair:
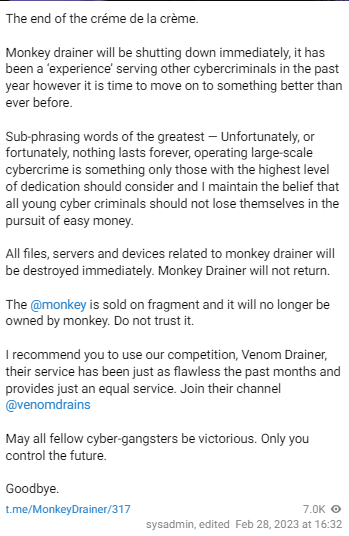 Monkey Drainer’s retirement message
Monkey Drainer’s retirement messageNow, did they really retire, or did they choose to rebirth themselves under a new name? Only time will tell.
Venom and Pussy Drainers, which appeared just a month before Monkey Drainer’s retirement, were able to claim their brutally abandoned customers.
In the month following the disappearance of Monkey Drainer, at least four drainer crews invested in the landscape: Inferno Drainer, MS Drainer, Pink Drainer, and Angel Drainer, while Venom disappeared in April 2023.
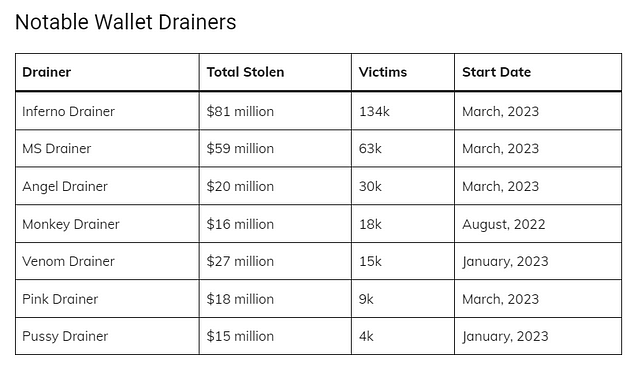 Source: ScamSniffer
Source: ScamSnifferIn November 2023, the most damaging wallet drainer kit in crypto history, Inferno Drainer, announced that it would also retire.
“A big thank you to everyone who has worked with us. We hope you can remember us as the best drainer that has ever existed and that we succeeded in helping you in the quest to make money. Goodbye.” — Inferno DrainerBut, this time around, breaking with their forefathers’ tradition, they choose not to shut down.
All files, servers, and devices related to their kit would keep running so that their faithful customers would have the time to transition smoothly to a new wallet drainer, or so they said.
The direct consequence of this move is that since their retirement, with no date announced for the final unplug, scammers kept on actively using it and have reaped in six months about $100 million, stolen from around 50,000 new victims, according to blockchain security firm ScamSniffer.
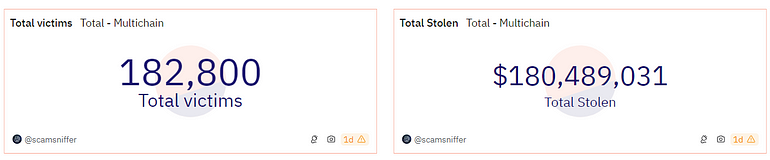 Source: ScamSniffer
Source: ScamSnifferThey were banking even more during their inactive period than they did before, very likely profiting off the bull run of January 2024, with its influx of massive liquidity and new entrants.
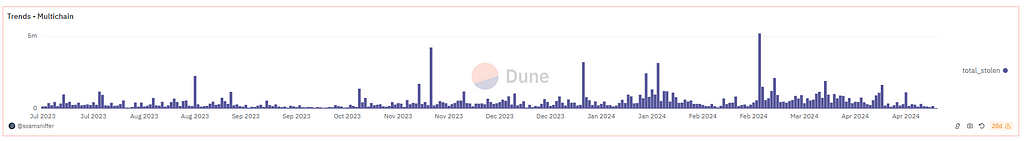 Source: ScamSniffer
Source: ScamSnifferThe vacuum left by Inferno Drainer “semi departure” was quickly filled by Pink Drainer.
Contrary to its cute name, Pink Drainer has been a devastating force over the past year in the crypto space, with more than $85 million stolen from crypto wallets through their SaaS wallet drainers.
To everyone’s relief, they announced in May 2024 that they would retire promptly.
But apparently, crypto users cannot take a breath. Guess who’s back days after this announcement?
Inferno Drainer, the crypto wallet boogeyman.
That was a very short retirement, indeed.
When Inferno Drainer announced their comeback, not even days after Pink Inferno closed down shop, they claimed that during their absence, more than $125 million had been drained by their clients, amounting to over $250 million stolen through them in the space of one year.
Figures much higher than those collected by ScamSniffer, which could be either the truth or a sales pitch.
The most interesting part of their comeback message is that, in the same breath, they claim that at the root of their comeback are their clients. They state that it was the loyalty of their clients post-shutdown that “made it clear they desired [their] return” and that “major competitors shutting down” and “incompetent drainers” attempting to resell the drainer would penalize them.
It reads as if it was almost against their will, and they have to return at the drop of a hat to save their poor scammers, sorry, clients.
This is in sharp contrast with the beginning of their message, where they state white on black that during the past 6 months, they were busy “operating privately, making drainer and team way much better,” and that they were coming back better than ever with “new staff, new ways to work, new support and new features.”
In short, they never retired.
They just “paused” their drainer to improve it away from scrutiny.
 Source: Plum on Twitter
Source: Plum on TwitterBut Inferno Drainer hasn’t only been busy bringing to the table a new, even more powerful turnkey wallet drainer offer with ‘free web dev & hosting’ included over the past months.
They have also had their hands full trying to obfuscate their tracks and cash out their ill-gotten funds.
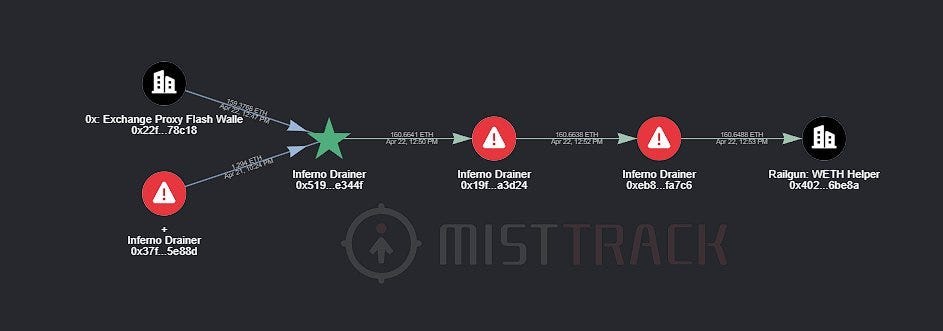
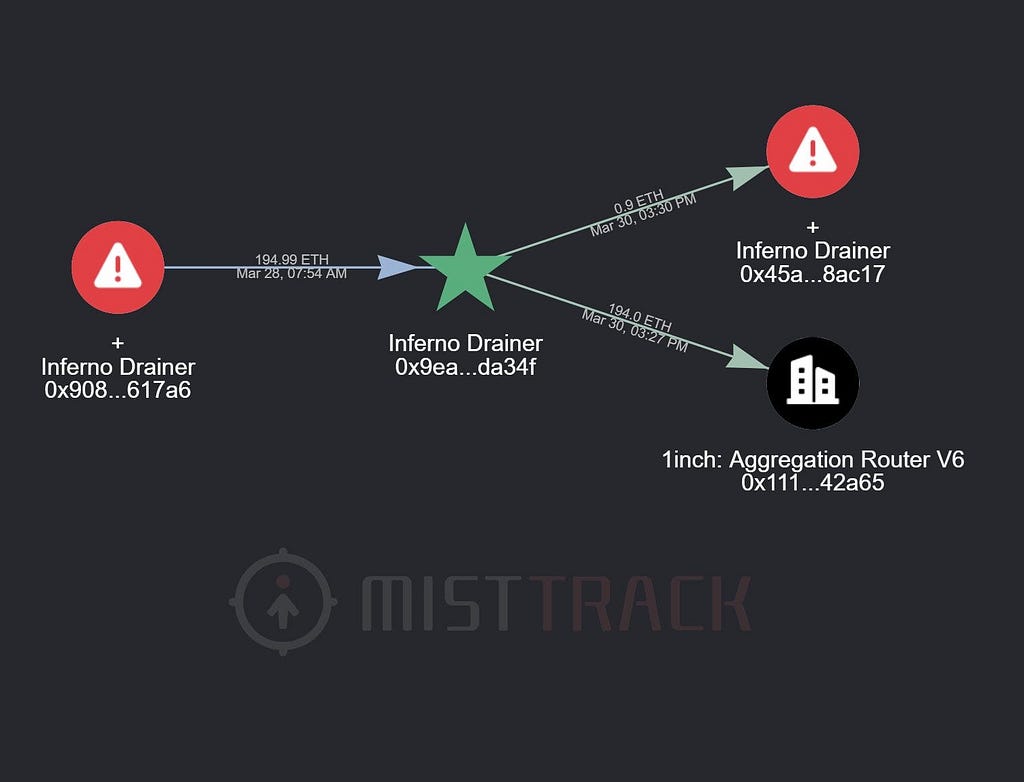
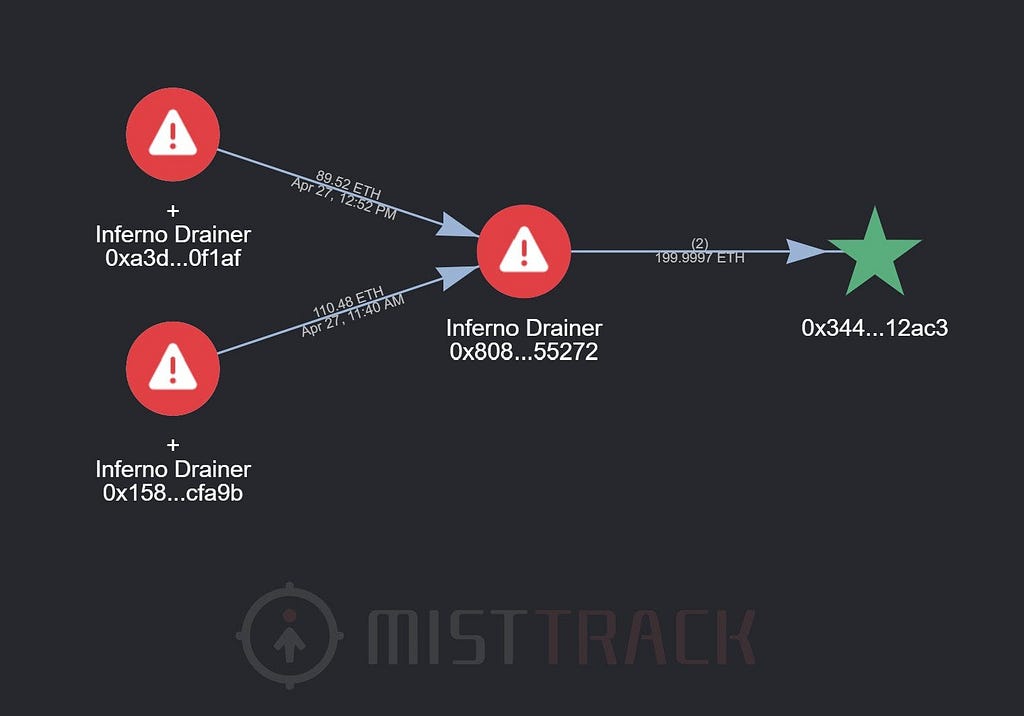
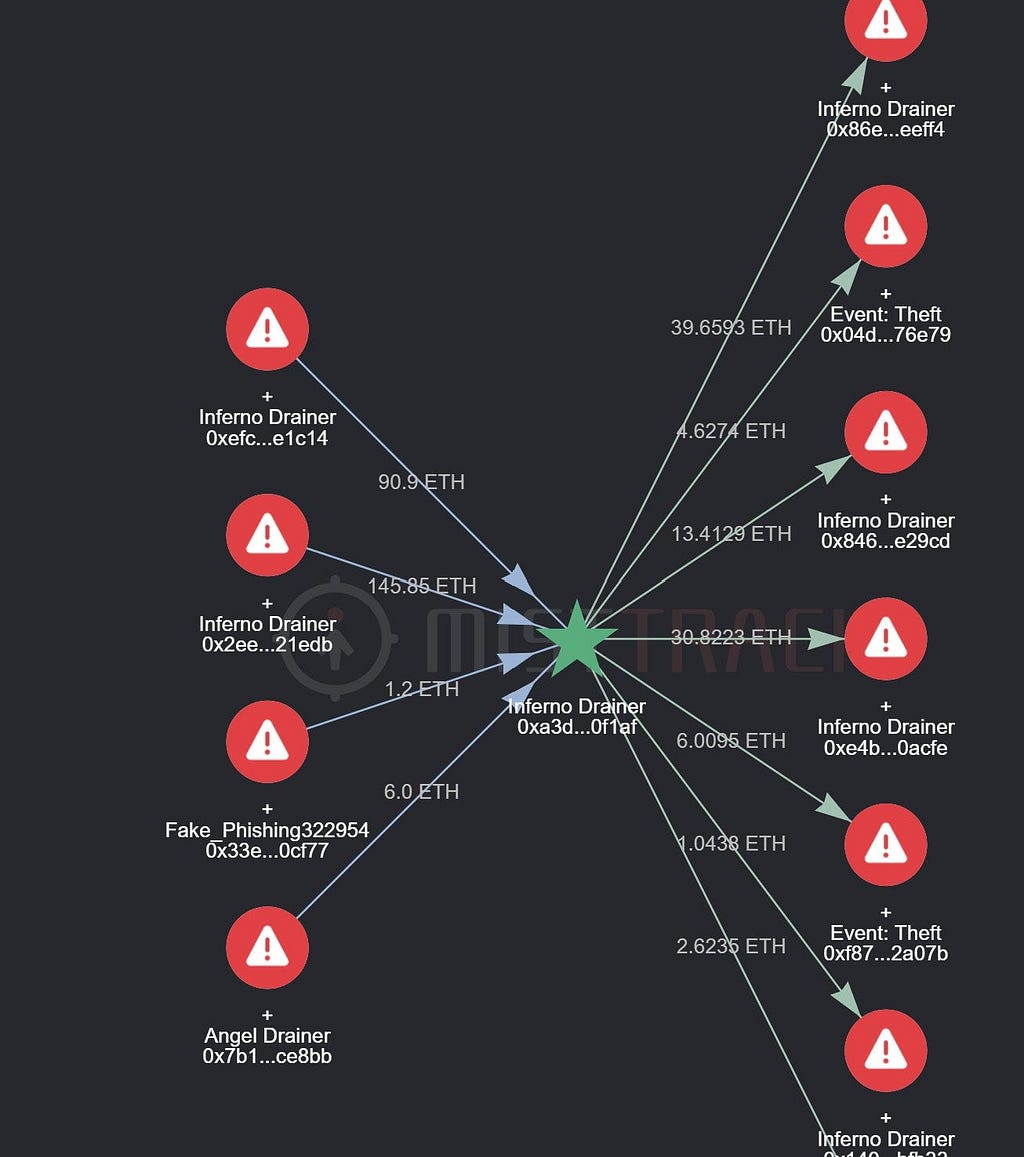 Money Laundering Attempts Recorded by Mistrack — Source: Mistrack’s Twitter
Money Laundering Attempts Recorded by Mistrack — Source: Mistrack’s TwitterIn this bizarre, possibly premeditated game of musical chairs aside, wallet drainers demonstrate hyper-flexibility by constantly finding new ways to bypass threats posed by blockchain security firms, thus evading safeguards meant to protect users.
Alternatively, they find new spaces to target, as they are now transitioning to the newly launched TON blockchain, which is full of unseasoned new entrants and liquidity but lacks any form of security protection against them.
But wallet drainers would be nothing without the thousands, if not tens of thousands, of users they have, as well as the strategies implemented to maximize the damage to their victims.
Among all the strategies used by wallet drainers users, one stands out: permit phishing.
Permit Phishing: The Most Efficient and Damaging Crypto Phishing Method
According to Scam Sniffer’s data, almost 90% of the hundreds of millions stolen through crypto wallet drainers during H1 2024 were taken via a simple signature method known as Permit/Permit2 phishing.
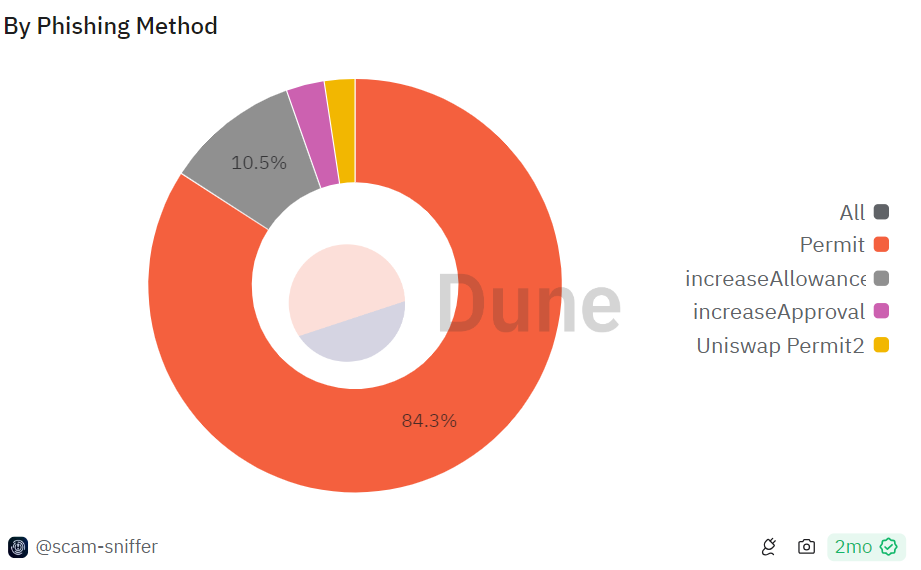 Crypto Phishing Methods- Source: Scam Sniffer
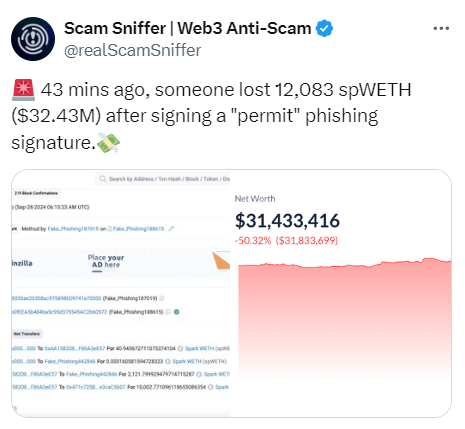
Crypto Phishing Methods- Source: Scam SnifferNotably, in September 2024, a single victim lost over $32 million in a permit phishing scam.
The Permit function was introduced in the ERC20 protocol through EIP-2612 (Ethereum Improvement Proposal 2612).
EIP-2612 allows token holders to approve transfers with a signature instead of a transaction.It allows token approvals to be signed off-chain and submitted by someone else on-chain.One of the primary benefits of the gas efficiency of this functionality is that by allowing users to approve tokens and transfer them in a single transaction, it significantly reduces the gas fees associated with separate transactions.
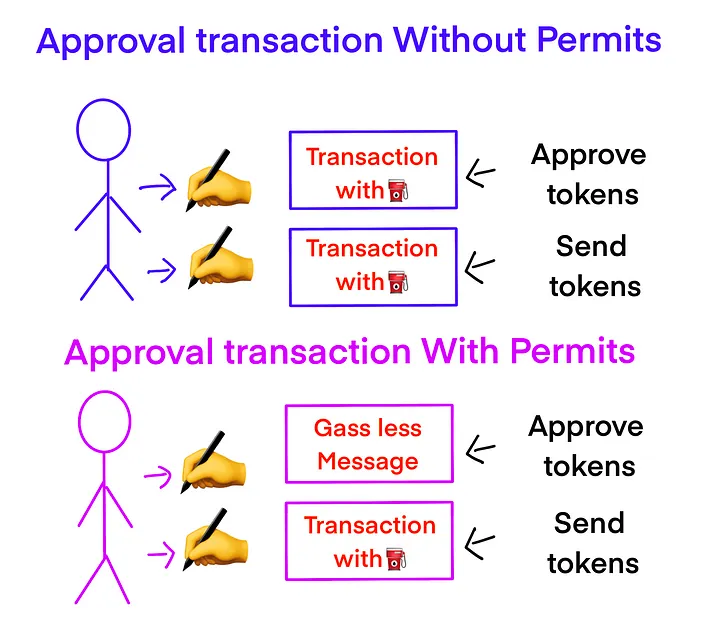 Source: Anett Anett
Source: Anett AnettOff-chain approvals also contribute to this efficiency, as signing approvals off-chain and then submitting them on-chain lowers the number of required on-chain operations.
Users no longer need to go through the time-consuming process of submitting separate transactions for approval and transfer, which streamlines interactions with decentralized applications (dApps). This also leads to better integration with services that require token approvals, enhancing the overall user experience.
In terms of security, EIP-2612 provided notable enhancements. Users can delegate approval without needing to trust the dApp with direct control over their tokens by signing approvals off-chain.
This approach also limits the need for continuous on-chain interactions, thereby reducing exposure to on-chain vulnerabilities. EIP-2612 also includes time-limited permissions, allowing approvals to have expiration times. This feature ensures that permissions are only valid for a specific period, minimizing the risk of long-term unauthorized access.
So how did an EIP that was supposed to reinforce the security of crypto users end up becoming one of the most powerful tools used by crypto criminals to siphon wallets?It’s very simple, really.
Let’s say Alice, unfortunately, clicks on a phishing link and ends up on a malicious website posing as her favorite DeFi platform. The website asks Alice to sign a permit message disguised as a routine verification. This does not trigger Alice’s suspicion because 1) she was taught that funds are stolen solely through approvals/transactions, and 2) she is used to such requests.
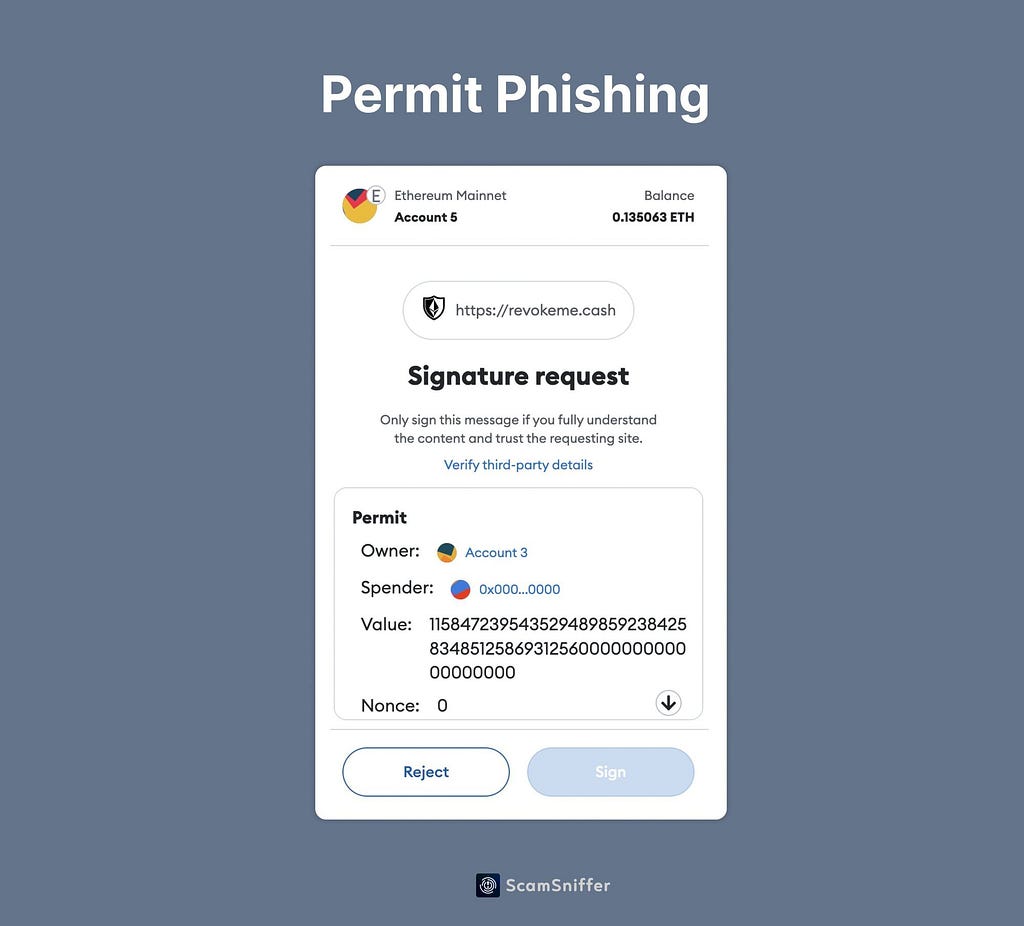 Source: ScamSniffer
Source: ScamSnifferAlice signs the message. Bob, the scammer, takes the signed permit and submits it to the token contract, granting him approval to spend Alice’s tokens. Bob then executes a transfer of tokens from Alice’s account to his own, successfully draining her funds.
That’s how a simple signature can steal a victim’s crypto assets and why it makes up the bulk of wallet drainer phishing activity targeting users.
Wallet drainers as a SaaS have opened Pandora’s box of phishing, with efficient, powerful entities coordinating to take turns while others regroup, returning more sophisticated and dangerous each time.Whatever unfolds in Q4 2024, it’s clear that wallet drainers and their operators have already owned the year 2024.What can we expect for the last quarter of 2024?
Probably more of the same: the Lazarus Group continuously targeting crypto actors, private key exploits rampant, and wallet drainers emptying out the crypto of your average (or not-so-average) Joe at an accelerated pace.
About us
Nefture is a Web3 real-time security and risk prevention platform that detects on-chain vulnerabilities and protects digital assets, protocols, and asset managers from significant losses or threats.Nefture core services include Real-Time Transaction Security and a Threat Monitoring Platform that provides accurate exploit detections and fully customized alerts covering hundreds of risk types with clear expertise in DeFi.
Almost $1 Billion Lost: Q3 2024 Crypto Crime Report was originally published in The Capital on Medium, where people are continuing the conversation by highlighting and responding to this story.

 3 weeks ago
25
3 weeks ago
25






 English (US) ·
English (US) ·